Release 2 (9.0.2)
Part Number A90146-01
Home |
Solution Area |
Contents |
Index |
| Oracle9i Application Server Security Guide Release 2 (9.0.2) Part Number A90146-01 |
|
Oracle9i Application Server (Oracle9iAS) provides a comprehensive security framework supporting all Oracle9iAS components, as well as third-party and custom applications deployed on the application server. The framework is based on Oracle9iAS Single Sign-On for authentication, Oracle Internet Directory for authorization and centralized user provisioning, and the Oracle Java Authentication and Authorization Service (JAAS) provider for security in Java2 Enterprise Edition (J2EE) applications.
This chapter provides an overview of the security architecture and features of Oracle9iAS in the following topics:
Oracle9iAS is a reliable, scalable, secure, middle-tier application server designed to support a company's evolution into an e-business. With this product, the technological complexity of assembling a complete middle-tier Internet foundation is managed for you. The technological foundation that Oracle9iAS provides can grow with your business. It can start small and support growing numbers of users and sophisticated functionality on all of your Web sites.
Oracle9iAS includes components which provide a general framework for development and deployment of applications, as well as components that provide specific application services or functionality. This chapter focuses on the security services provided by the Oracle9iAS Infrastructure, which includes Oracle9iAS Single Sign-On Server and Oracle Internet Directory, an LDAP, version 3-compliant directory service. It also provides an overview of the security services provided by Oracle HTTP Server, Oracle9iAS Web Cache, Oracle9iAS Portal, and JAAS (Java Authentication and Authorization Service), which provide support for a broad range of application development and deployment strategies.
Oracle9iAS provides a solid framework for building and deploying Web applications using the Apache-based Oracle HTTP Server, Oracle9iAS Containers for J2EE, and Oracle9iAS Portal, which use the advanced security functionality provided by Oracle9iAS Infrastructure. Oracle9iAS Infrastructure consists of Oracle9iAS Metadata Repository, Oracle Internet Directory, Oracle9iAS Single Sign-On, and Oracle Management Server. Oracle9iAS security starts from the well-tested and highly configurable Web security services provided by Oracle HTTP Server, adds a comprehensive set of Web single sign-on services, and extends them further with centralized user provisioning that is available in Oracle Internet Directory, an LDAP, version 3-compliant directory service. In addition, Oracle9iAS provides the Oracle implementation of Java Authorization and Authentication Services (JAAS) for J2EE application security, and extensive portal authorization and application integration mechanisms. Oracle9iAS also supports secure access to Oracle database systems using Oracle Advanced Security.
This section introduces the application server security architecture, and shows how the different elements provide the security features required in an Internet environment.
|
See Also:
"What to Install to Get the Security You Require" for a description of Oracle9iAS Infrastructure and a summary of software requirements for security. |
Figure 2-1, described below, illustrates how the elements of Oracle9i Application Server function together.
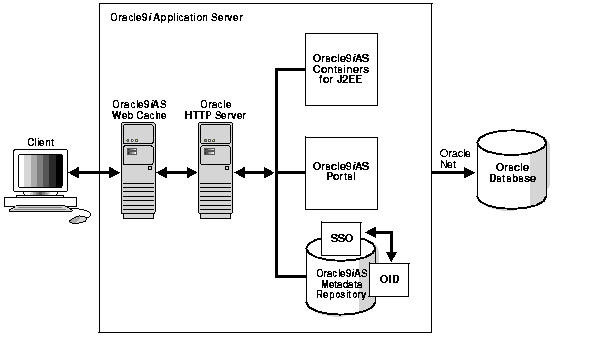
The Oracle9i Application Server PKI implementation provides a variety of security services, in compliance with industry-standard specifications. It incorporates a whole suite of products and features, including the following:
The Secure Sockets Layer (SSL) is an application layer protocol that can be employed for certificate-based authentication. All of the major components of Oracle9iAS support SSL.
|
See Also:
"Authorization, Authentication, and SSL in Oracle9iAS" for information about SSL support in Oracle9iAS. |
An Oracle wallet is a container in which certificates and trusted certificates are stored and managed. These data structures securely store a user private key, a user certificate, and a set of trusted certificates (the list of root certificates which the user trusts).
This is a Java-based application that security administrators use to manage public-key security credentials on both Oracle clients and servers. It creates an Oracle wallet. Oracle Wallet Manager creates a public-private key pair and manages credentials for a user. It issues PKCS#10 certificate requests to the certificate authority, and installs the certificate in the wallet. It ships with trusted certificates from VeriSign, RSA, and Baltimore CyberTrust, and can use a site's own in-house certificate authority.
|
See Also:
Chapter 5, "Using Oracle Wallet Manager" for information about Oracle Wallets and Oracle Wallet Manager. |
Oracle Internet Directory, an LDAP V3-compliant directory built on the Oracle9i database, helps to enable PKI-based single sign-on. It enables you to securely manage the user and system configuration environment, including security attributes and privileges, for users authenticated using X.509 certificates. Oracle Internet Directory enforces attribute-level access control, enabling the directory to restrict read, write, or update privileges on specific attributes to specific named users (for example, a security administrator). It also supports protection and authentication of directory queries and responses through SSL encryption.
|
See Also:
"Centralized User Provisioning and Single Sign-On in Oracle9iAS" for information about Oracle Internet Directory and centralized user provisioning in Oracle9iAS. |
Oracle9iAS provides several installation options so you can install only the functionality that you require. The two primary software installations that involve security functionality are
This installation provides single sign-on (SSO), LDAP directory, and centralized management features. It installs Oracle9iAS Metadata Repository, Oracle Internet Directory, Oracle9iAS Single Sign-On, and Oracle Management Server, and it configures all except Oracle Management Server. You must first install and configure the infrastructure before installing Oracle9iAS components with the Oracle9i Application Server Installation.
This installation provides several installation types that allow you to choose which components of Oracle9iAS you want to install. For example, you can select the basic installation type, "J2EE and Web Cache," which includes a Web server, a Java runtime environment, and a Web cache. Or you can select to install all components of Oracle9iAS, which includes the basic set of software plus the functionality to enable portals, wireless applications, business intelligence, and messaging.
The components in this type of installation can be enabled to support PKI over SSL without installing Oracle9iAS Infrastructure. However, the infrastructure supports functionality that is not directly related to security for many of the components in the Oracle9i Application Server Installation.
Table 2-1 lists what you need to install and configure to get the security features that you require for your Web sites and applications.
When you install Oracle9iAS Infrastructure and use Oracle Internet Directory for security management, a default security implementation is provided. These default security settings include a default user password policy. This password policy applies to all user entries that are managed in the user container that is identified by the subscriber's user searchbase (orclcommonusersearchbase) in the directory. Table 2-2 lists the default user password policy in Oracle9iAS when Oracle Internet Directory is used for security management.
|
See Also:
|
When you install the Oracle9iAS Infrastructure, you enable single sign-on (SSO) and centralized user provisioning. SSO and centralized user provisioning are provided by Oracle9iAS Single Sign-On and Oracle Internet Directory. When these services are installed, the installation program automatically performs the following tasks that are related to security:
The security services that are provided by Oracle9iAS Infrastructure are described in the following topics:
When you install Oracle9iAS Infrastructure, all users and groups who access Web applications are created, stored, and maintained in Oracle Internet Directory and authenticated with Oracle9iAS Single Sign-On.
In this model, the following steps outline how users are created and authenticated so they can access Web applications:
Alternatively, users can also enter a URL for a specific Web application in their browsers, which causes the Oracle9iAS Single Sign-On login dialog box to appear so they can be authenticated before accessing the application.
Centralized user provisioning and single sign-on are important features of the comprehensive Oracle9iAS security framework. Together, these features reduce security risks and increase the efficiency of security administrators and employees.
The centralized user provisioning that is provided by Oracle Internet Directory, an LDAP version 3-compliant directory, makes maintaining separate stores of user identity and security information in various components of the application server unnecessary. Because all user identity and security information is stored in a central repository, administrators can manage users in one place, thereby reducing the time it takes to manage this information and reducing the likelihood that user identities can be comprised.
Oracle9iAS also supports single sign-on (SSO) to Web-based applications. There are a number of reasons why businesses are considering SSO. These include the increasing use of Web-based e-business applications which companies are deploying for use by employees, customers, and partners. Without SSO, each user must maintain a separate identity and password for each application accessed. When users must maintain multiple user names and passwords, it is easier for them to forget or lose them. When users must maintain multiple user names and passwords for various applications and information, administrators must keep track of them. In brief, maintaining multiple accounts and passwords for each user is insecure and expensive.
Using centralized user provisioning and single sign-on improves employee efficiency and makes your Internet infrastructure secure.
Oracle Internet Directory consolidates the management of users and groups in Oracle9iAS. It retrieves and stores information about dispersed users, groups, and network resources.
The directory implements version 3 of the Lightweight Directory Access Protocol (LDAP), which is the Internet standard for directory services. LDAP is based on the earlier ISO X.500 Directory Access Protocol (DAP) standard, but simplifies that standard considerably, enabling LDAP to be more efficient, straightforward, and easier to implement. LDAP is especially suited for deployment with "thin-client" applications that are developed for an Internet environment.
Oracle Internet Directory is not a security product, but rather a technology for managing enterprise data, including security data such as user names and passwords for Oracle9iAS Single Sign-On.
Each LDAP directory server instance looks like the configuration in Figure 2-2.
|
See Also:
For complete information about Oracle Internet Directory, see the following documents, which are available in the Oracle9iAS Documentation Library unless otherwise specified here:
|
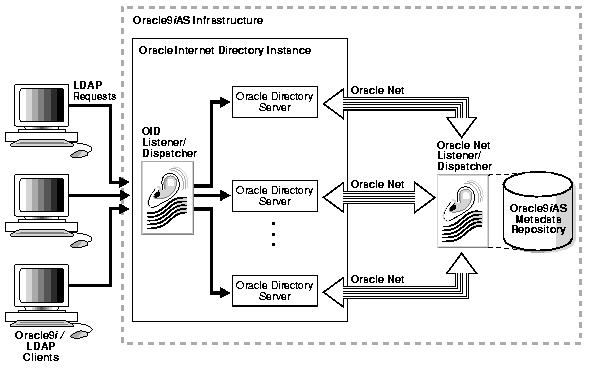
Oracle Internet Directory offers comprehensive and flexible support for directory access control. This includes entry level, attribute level, and prescriptive access control to provide varying levels of security to meet the specific needs of enterprise and service providers. An administrator can grant or control access to a specific directory object or to an entire directory subtree. The directory implements three levels of user authentication: anonymous, password-based, and certificate-based using Secure Sockets Layer (SSL) Version 3 for authenticated access and data privacy.
In addition, the directory provides many powerful features you can use in an enterprise or hosted environment to control access to application metadata--the information governing how applications behave and who can access them. To do this, you deploy the directory for administrative delegation. Using this deployment, a global administrator can give department administrators access to the metadata of applications in their departments. These department administrators can then control access to their department applications.
Oracle Internet Directory offers the following important security benefits:
A directory stores all information pertaining to Oracle software in a root container called the Oracle Context. A starter Oracle Context is automatically created for you when you install the Oracle9iAS Infrastructure, but you can create an Oracle Context under any entry in the DIT (directory information tree). Oracle Net Configuration Assistant is a tool you can use to configure directory access. It displays a list of published directory entries as suggested locations from which you can build an Oracle Context.
Figure 2-3 shows a simplified view of the starter Oracle Context that is set up when you install Oracle9iAS Infrastructure. The starter Oracle Context looks very similar to a directory subtree with Products and Groups containers subsumed under the root Oracle Context. In this figure, there are containers for two products under the Products container, plus a container that holds all of the entries which are common to all of the Oracle9iAS products represented in the DIT.
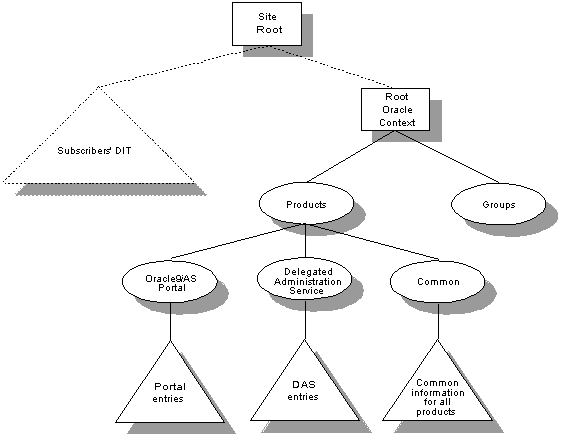
An Oracle Internet Directory node is implemented as an application running on the Oracle9iAS Metadata Repository. To communicate with the repository, which may be on the same system or on a different one, Oracle Internet Directory uses Oracle Net Services, the Oracle platform-independent database connectivity solution. This relationship is illustrated in Figure 2-4.
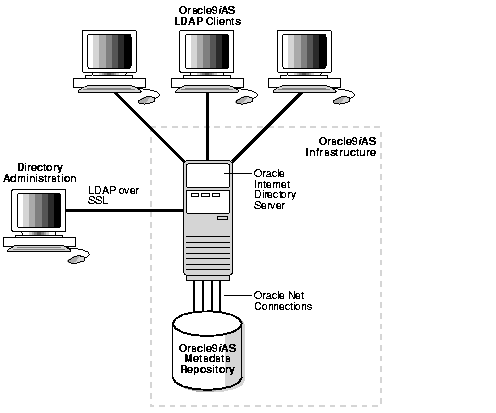
DAS is a Web-based GUI tool that directory administrators can use to create users, and users can use to modify their own personal data (such as addresses, phone numbers, and photos), without an administrator's intervention. Using DAS, users can also search other parts of the directory to which they have access, so administrators are free to perform other tasks.
This tool relies on small Java programs, called servlets. Servlets receive requests from clients, process those requests (by either retrieving or updating data in the directory), then generate results, which they send back to clients.
Oracle9iAS Single Sign-On (SSO) technology provides single sign-on for Web users. It is designed to work in an environment such as that provided by Oracle9i Application Server, where multiple Web-based applications are accessible through a portal. The Oracle strategy for SSO encompasses a variety of technologies. For the growing field of Web-based applications, Oracle has developed an SSO framework, Oracle9iAS Single Sign-On, which is specifically designed to provide Web SSO.
The Oracle9iAS Single Sign-On approach has a number of benefits. It provides a framework for secure SSO from browser clients to Web-based applications, including Oracle applications and tools, through standard protocols. It supports both partner applications, which take full advantage of the SSO framework, as well as external applications for support of legacy and third-party products. Partner applications work within the SSO framework and rely on the SSO service for authentication of users; external applications continue to use their own user names and passwords. The Oracle9iAS Single Sign-On approach is based on cookies, which are created both by partner applications and by a centralized Oracle9iAS Single Sign-On server.
This section includes these topics:
Oracle9iAS Single Sign-On is composed of the following components, which are described in the following sections:
Oracle9iAS Single Sign-On server is the core of Oracle SSO technology. It is well integrated with Oracle HTTP Server through mod_osso, which is an HTTP server plug-in that routes HTTP requests that require SSO to the Single Sign-On server for initial authentication. In addition, it allows management of user information in Oracle Internet Directory. Oracle9iAS Single Sign-On also permits integration with SSO technologies for other, non-Oracle applications. It supports PKI client authentication, which enables PKI authentication to a wide range of Web applications. By means of an API, Oracle9iAS Single Sign-On can integrate with third-party authentication mechanisms such as Netegrity Site Minder.
Two different types of applications can use Oracle9iAS Single Sign-On:
The mod_osso component of Oracle9iAS Single Sign-On is a module that plugs into Oracle HTTP Server. It enables the HTTP listener as a partner application that can use the Single Sign-On server to authenticate users. Once mod_osso is installed and configured, Web applications can register URLs that require SSO authentication with the module. Then when URL requests are received by the HTTP server, mod_osso detects which requests require SSO authentication and redirects them to the Single Sign-On server. After the Single Sign-On server authenticates the user, it passes the user's authenticated identity back to mod_osso in a secure token, or cookie. The module retrieves the user's identity from the cookie and propagates the user's identity information to applications running in the HTTP server instance. The module can propagate the user's identity information to applications running in the CGI, those running in Oracle9iAS Containers for J2EE, and it can also authenticate users for access to static files.
This section includes these topics:
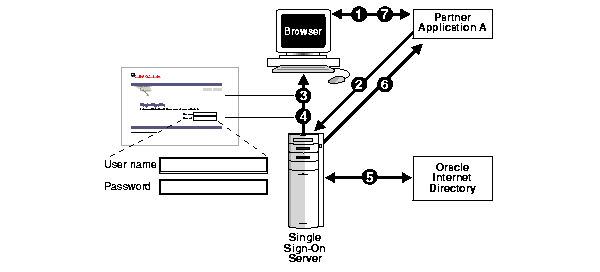
When a user attempts to access a partner application, which includes mod_osso, for the first time, he is redirected to Oracle9iAS Single Sign-On. Oracle9iAS Single Sign-On checks to determine whether the user has a valid SSO cookie set; if not, it requests that the user authenticate by submitting a user name and password. Once the user has done so, the Oracle9iAS Single Sign-On verifies the password and then sets an SSO cookie in the user's browser. Henceforth, the client sends this cookie along with all HTTP interactions with Oracle9iAS Single Sign-On, authenticating itself and avoiding the need to reauthenticate for as long as the cookie is valid. Figure 2-5 shows how partner applications are authenticated with Oracle9iAS Single Sign-On.
The SSO cookie is encrypted by Oracle9iAS Single Sign-On, so that it cannot be set or read by a third party. Cookies expire after a certain period of time, as set by the administrator (typically 8 hours); or when users shut down their browser. SSO cookies are not persistent, and are deleted when a browser is shut down.
Note that interactions between the Oracle9iAS Single Sign-On Server, browser clients, and applications are all by means of standard HTTP. No special requirements are placed on clients, other than that they support cookies. It is recommended that SSL be enabled between Oracle9iAS Single Sign-On Server and the client to prevent user names, passwords, and SSO cookies from being intercepted by a third party, who could possibly use them to spoof the Oracle9iAS Single Sign-On Server.
Once a user has been authenticated and an SSO cookie has been set, Oracle9iAS Single Sign-On directs the user back to the partner application, and includes an encrypted token in the partner application URL. This token contains the user's identity and session information. The token is encrypted in a key which is shared only by Oracle9iAS Single Sign-On and the partner application. This assures the partner application that the token is authentic, and was created by Oracle9iAS Single Sign-On.
When the partner application receives and decrypts the URL token, it can determine whether to grant the authenticated user access to the application. To grant access, it sets a partner application cookie in the user's browser. The client sends the partner application cookie along with subsequent HTTP requests to the partner application. This allows the application to identify and grant access to the user, without having to redirect the user to Oracle9iAS Single Sign-On for authentication. Partner application cookies, like SSO cookies, expire after a certain period of time. Unlike SSO cookies, partner cookies may be persistent or non-persistent (that is, they may or may not survive the shutdown of a browser). The expiration period for a partner application cookie is determined by the application, and may be different than the SSO cookie expiration time. Figure 2-5 shows how authentication with partner applications works.
As with SSO cookies, it is recommended that SSL encryption be used to protect the cookie exchange between browser and partner application.
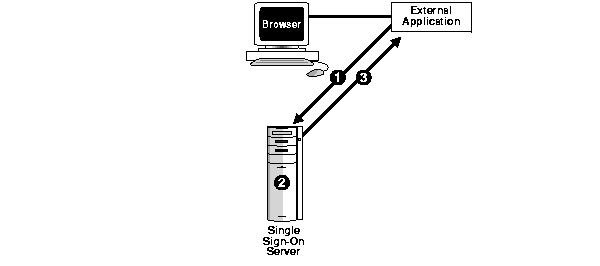
External applications cannot accept an authenticated identity directly from Oracle9iAS Single Sign-On. Oracle9iAS Single Sign-On provides SSO to external applications which support it by means of Web forms. Oracle9iAS Single Sign-On provides SSO by means of a password store, which maintains application-specific user names and passwords in a table within Oracle9iAS Single Sign-On. Access to this table is restricted by Oracle9iAS Single Sign-On, and passwords are further protected by encryption. When a user who has been authenticated by Oracle9iAS Single Sign-On needs to access an external application, Oracle9iAS Single Sign-On retrieves the user's user name and password for that specific application from the password store, formats them in the appropriate Web form, and submits them to the application. This is done transparently to the user. Figure 2-6 shows how authentication to external applications works.
Note that SSL encryption between Oracle9iAS Single Sign-On and external applications can be used to prevent exposure of application passwords in the network.
LDAP directories are increasingly used as a single source of enterprise-wide information about users. These directories provide a convenient mechanism for provisioning (creating and configuring) and managing users who use multiple applications or servers in an enterprise. This is because LDAP is a widely supported, Internet-standard protocol, and because an LDAP directory can be used as a convenient, single source of information about users, accessible throughout the enterprise. Oracle Internet Directory is particularly well suited for this type of application, because it provides a secure, fast, scalable, and available directory service.
Oracle9iAS Single Sign-On allows SSO user names and passwords to be verified using Oracle Internet Directory. This is the default, unless you specify otherwise. When a user submits an SSO user name and password as part of the initial authentication, Oracle9iAS Single Sign-On performs an LDAP compare against Oracle Internet Directory using this user name and password. If the LDAP compare succeeds, the SSO user name and password are considered to be verified.
PKI authentication is beginning to replace passwords in many applications. In Web-based applications, PKI authentication is typically performed through an exchange of X.509 certificates, as part of a Secure Sockets Layer (SSL) session establishment. PKI by itself can be used to provide SSO, because a user with a certificate can authenticate to multiple applications without entering a password.
Users can authenticate to Oracle9iAS Single Sign-On by means of PKI. This provides SSO both to Web-based applications supported by Oracle9iAS Single Sign-On, and to other PKI-enabled applications. Instead of providing an SSO user name and password, users authenticate to Oracle9iAS Single Sign-On by means of SSL with client and server X.509 certificate exchange. Authentication to partner and external applications can then be performed using the cookie-based approach described previously. The directory translates the certificate identity to the SSO user name.
Benefits of this approach are that applications which work within Oracle9iAS Single Sign-On framework are PKI-enabled automatically when Oracle9iAS Single Sign-On is PKI enabled. Oracle Internet Directory assumes responsibility for name mapping. Moreover, because getting and checking a cookie requires fewer system resources than performing an SSL exchange, using PKI for initial authentication to the SSO framework and cookies for authentication to partner applications has better performance than a PKI-only authentication approach. For Web applications which are characterized by many short-lived sessions, this leads to significant improvement in server performance and throughput.
Finally, enabling Oracle9iAS Single Sign-On for PKI allows users to authenticate to Oracle Applications using PKI. In this way, Oracle Applications can participate in the SSO framework as partner applications.
Oracle9iAS Single Sign-On provides SSO for Web client access to Web servers. Web servers are increasingly deployed as the middle tier in a multitier architecture, where they provide access to a back-end tier database. Users of Web applications that require access to the database should not have to supply a database user name and password for access to data stored there. Although Oracle9iAS Single Sign-On does not support non-Web based applications, the Oracle database includes features specifically designed to support secure access to databases through multitier architectures.
Oracle9iAS provides a number of mechanisms for accessing the database and invoking applications on it. The most commonly used of these fat-client JDBC and mod_plsql, a plug-in to Oracle HTTP Server that allows Oracle9iAS to invoke database applications written in the Oracle database programming language, PL/SQL. Because fat-client JDBC and mod_plsql access an Oracle database with the Oracle client-server networking protocol, Oracle Net, developers who use fat-client JDBC or mod_plsql can use Oracle Advanced Security, an option of Oracle9i Database Server. Oracle Advanced Security, which provides encryption, integrity protection, and advanced authentication, can be used to protect data exchanged between Oracle9iAS and an Oracle database.
|
See Also:
|
Each major component of the application server provides a set of basic security services, which authorize and authenticate users with or without SSL, that can be used individually or in conjunction with other components. This section describes the basic security services that are available in the following Oracle9iAS components:
Oracle HTTP Server is the Web server component of Oracle9iAS. It is based on the Apache HTTP Server. The Apache open source Web server is among the most widely-adopted Web server products; it supports a rich set of existing applications, and provides a flexible and well-understood security model. Apache is a very well-tested platform on which to deploy secure applications. Customers familiar with Apache should find it easy to build and deploy secure Web applications using Oracle HTTP Server.
This section describes the security features of Oracle HTTP Server in the following topics:
Oracle HTTP Server extends Apache with a variety of standard enhancements called "mods," which is a shortened form of module. It also includes mods that have been developed by Oracle Corporation. It allows users with Web browsers to access Oracle9iAS using standard Web protocols. It provides an HTTP listener, which supports HTTP and secure HTTP, or HTTPS, and serves up information to users in standard HTML format. It provides access to both static Web pages and dynamic content.
Oracle HTTP Server security services include the ability to restrict or allow access to files and services based on the identity of users established by means of basic authentication, by client- supplied X.509 certificates, and by IP or hostname addresses.
Another important feature of Oracle HTTP Server security is protection of data exchanged between clients and the server. This is provided by means of the SSL protocol, which also provides data integrity and strong authentication of both users and HTTP servers.
In addition, Oracle HTTP Server provides logging and other facilities needed to detect and resolve intrusion attempts. It provides integration with the other Oracle9i Application Server components, such as mod_osso, which enables the HTTP server to receive and route requests for single sign-on services to Oracle9iAS Single Sign-On server. Oracle HTTP Server is also well integrated with other Oracle products such as Oracle applications and the database. In this way, the Oracle HTTP Server provides a comprehensive set of security services for building and deploying Web applications.
|
See Also:
|
When URL requests arrive at Oracle HTTP Server they are processed in a number of steps which are implemented by means of a module or plug-in architecture common to many Web servers.
Oracle HTTP Server access control is based on Apache access control mechanisms which allow the server administrator to restrict access to particular files, directories, or URLs on the server. For each restricted object on the server, the administrator can use a directive in the main configuration file, httpd.conf, to specify that access to the object is denied or allowed, based on the value of one or more attributes associated with the requester. The administrator can configure directives such as deny, allow, and order to inhibit further processing, based on user attributes such as hostname, IP address, or browser type. Restrictions can be applied to particular files, directories, or URL formats.
In many applications it is desirable to control access to resources on the Web server based on user identity. Oracle HTTP Server provides several mechanisms for user authentication, including client authentication over the Single Sockets Layer (SSL) using X.509 certificates, user name/password pairs (as in basic authentication), and other forms. A server administrator can use a configuration directive in the httpd.conf file to specify that access to certain URLs is restricted to particular users.
The Secure Sockets Layer provides point-to-point security between Oracle HTTP Server and client browsers. Security-related services provided by SSL include authentication, authorization, confidentiality, and data integrity. The HTTP server supports SSL with a module developed by Oracle called mod_ossl. If you also need to implement PKI, Oracle Wallet Manager can be used to request, store, and manage certificates. These features are described in the following sections.
This Oracle HTTP Server module is a plug-in to the HTTP server that enables the server to use SSL. It is very similar to the OpenSSL module, mod_ssl. However, in contrast to the OpenSSL module, mod_ossl is based on the Oracle implementation of SSL, which supports SSL, version 3 and is based on Certicom and RSA Security technology.
|
See also:
|
Oracle9iAS makes it easy to build multitier systems using an Oracle database back-end repository. Oracle9iAS provides a number of mechanisms for accessing the database and invoking applications on the database. The most commonly used of these are JDBC and mod_plsql, a plug-in to the Oracle HTTP Server that allows the application server to invoke database applications written in the Oracle database programming language, PL/SQL. Because mod_plsql accesses the Oracle database using the Oracle client-server networking protocol, developers using mod_plsql can take advantage of Oracle Advanced Security to protect data exchanged between Oracle9iAS and an Oracle database. Oracle Advanced Security provides encryption, integrity protection, and advanced authentication services to Oracle database clients and servers. It supports industry standard encryption protocols such as SSL, and standard encryption algorithms including RSA RC4, DES, and 3DES.
It is also possible to use Oracle9i Database Server proxy authentication, which is designed to address a performance problem associated with three-tier application design. Specifically, it allows Oracle9iAS to access an Oracle9i database and get specific database user privileges without having to log out and log in again each time that the application server switches user contexts. Proxy authentication allows the application server to establish a single authenticated session using fat-client JDBC or mod_plsql with an Oracle9i database server, and act on behalf of multiple database users without having to submit separate authentication credentials for each user within the session. In addition, the database can use both the authentication identity of the application server and the identity of the user on whose behalf the application server performs proxy authentication. Thus, proxy authentication allows the database to delegate limited trust to a middle-tier application server without having to grant it superuser privilege on the database, or store multiple database user passwords in the application server. Proxy authentication is available with Oracle9i Database Server.
|
See Also:
|
This is a Java-based application that security administrators use to manage public-key security credentials on both Oracle clients and servers. Oracle Wallet Manager creates a public-private key pair and manages credentials for a user. It issues PKCS#10 certificate requests to the certificate authority, and installs the certificate in the wallet. It ships with trusted certificates from VeriSign, RSA, and Baltimore CyberTrust, and can use a site's own in-house certificate authority.
|
See Also:
Chapter 5, "Using Oracle Wallet Manager" for information about Oracle Wallet Manager and how to use it. |
This section describes several aspects of Oracle9iAS Portal security:
See Also:
Oracle9iAS Portal is an "enterprise portal" program, which provides a gateway to business information on corporate intranets. Although it is targeted at the corporate portal market, Oracle9iAS Portal can be scaled to provide access to much larger Internet communities.
Oracle9iAS Portal allows Oracle9iAS customers to organize their Web content and applications, and provide this to users in a logical, consistent Web portal format. It also provides a set of tools for creating and managing users and their access to Oracle9iAS Portal content. Enterprise portals, as both a consolidation and extension of existing market spaces, can utilize three powerful components:
This section provides an overview of the security features and architecture of Oracle9iAS Portal. Oracle9iAS Portal provides a comprehensive and extensible authorization model, based on user privileges and groups, for user access to content and applications on the portal. It also supports auditing of security events through its event logging service.
In the Internet computing model, where millions of users may potentially be accessing a portal, it is important to keep the representation of users as lightweight as possible. To manage large numbers of users and large amounts of data in a secure, scalable, and fault-tolerant way, Oracle9iAS Portal leverages the security and data management technology of the Oracle database.
Oracle9iAS Portal defines its own user accounts, which are referred to as "lightweight" because they do not each have a unique database schema associated with them in the Oracle database. By contrast, each Oracle9iAS Portal user account does correspond uniquely to an Oracle9iAS Single Sign-On user account. Oracle9iAS Portal provides a convenient mechanism to manage users of applications configured to use Oracle9iAS Single Sign-On.
When Oracle9iAS Portal is installed, a default set of user accounts is created. These include accounts for the portal administrator and a public account. The public account allows certain portal content to be publicly accessible; that is, it allows the content to be accessed by users who do not have their own Oracle9iAS Portal user accounts, or by users who do have accounts but who have not yet logged in.
|
See Also:
Table 6-10, "Default Oracle9iAS Portal Users" for a list of the users that are created by default when Oracle9iAS Portal is installed. |
Oracle9iAS Portal supports groups, which are used for two main purposes. Groups provide a convenient means of granting privileges to a collection of users in one action. In addition, certain attributes in the Portal system can be associated with a group, and if a user has a default group specified in his preferences, then those attributes can be applied to his session. Examples of these attributes include a default home page for a group, or a default style. Because a user can belong to multiple groups, he must specify a default group in his own profile so he can inherit group preferences. He should not specify any personal preferences that would override the group preferences.
Groups can be comprised of users, as well as other groups. This allows for construction of hierarchical groups. A user belonging to a subgroup of another group is a member of the parent group, by virtue of group membership. Privileges granted to the parent group are thus assumed by the subgroup user.
|
See Also:
Table 6-11, "Default Oracle9iAS Portal Groups" for a list of the groups that are created by default when Oracle9iAS Portal is installed. |
Oracle9iAS Portal is implemented as an Oracle9iAS SSO partner application for the purpose of user authentication. Note that users who are not authenticated may be allowed access to certain content on Oracle9iAS Portal by means of the public user account.
Authorization is the process of controlling access to various areas of Oracle9iAS Portal, based on the identity of the user. Once the user is identified, after going through the process of authentication, Oracle9iAS Portal determines the appropriate authorization of the user based on his identity.
Oracle9iAS Portal allows portal objects to be defined as public or private, depending on whether they are accessible to general Web users or only to trusted portal administrators. Objects which are public can still implement access control logic that is based on identity, in which case they must first obtain the user's identity from Oracle9iAS Single Sign-On. Once this has been done, the user's privilege to access the object can be determined. Oracle9iAS Portal provides an extensible set of privileges which are used to define the access control lists for each object in the portal.
One of the key features of Oracle9iAS Portal is the ability to integrate various applications into its framework to provide a seamless experience for those using it to access their business applications. Oracle9iAS Portal depends on Oracle9iAS Single Sign-On for this purpose, and supports varying degrees of integration between portal security and application security.
The tightest integration occurs when an application is implemented on Oracle9iAS Portal itself and obtains user identity directly from Oracle9iAS Portal. Such applications are called portal applications. Oracle9iAS Portal is a partner application for Oracle9iAS Single Sign-On, allowing it to obtain a user's identity from the Single Sign-On server. Portal applications obtain a user's identity directly from the once the user has authenticated by means of Oracle9iAS Single Sign-On.
Other applications accessible through Oracle9iAS Portal may be Oracle9iAS Single Sign-On partner applications or external applications, as described in the section on Oracle9iAS Single Sign-On. Partner applications need not be implemented on the portal itself, but do participate in the Oracle9iAS Single Sign-On authentication framework which Oracle9iAS Portal also uses. External applications maintain their own authentication mechanisms, and do not share directly in the authentication framework provided by Oracle9iAS Single Sign-On.
For increased security, Oracle9iAS Portal can be run in HTTPS mode over SSL. However, running Oracle9iAS Portal in HTTPS mode can significantly degrade this program's performance.
Besides monitoring activity which could indicate unauthorized system use, auditing of security related events is often the most effective means to ensure that authorized users adhere to system usage policies, and thus "keep honest users honest."
Oracle9iAS Portal has a logging service which logs certain security events and which can be invoked to log arbitrary events defined by portal applications. The reporting features of the Oracle9iAS Portal application building capabilities can then be leveraged to view the logged data. Event logging can be used to audit security events, to detect possible attempts to undermine system security, or to use the system in a way that is contrary to security policy.
Oracle9iAS Portal runs on the Oracle9i database. Many Oracle9iAS Portal events generate database events that can be audited.
|
See Also:
Chapter 6, "Configuring Oracle9iAS Portal Security" for more information about portal authorization, authentication, and application integration. |
This section introduces the primary security services provided by JAAS:
See Also:
JAAS includes two major features for authentication:
One of the biggest benefits of using JAAS is the ability to integrate applications with Oracle9iAS Single Sign-On. Most Web applications need single sign-on to enhance the user experience whether or not they are developed in Java.
This integration enables any Java application to participate in Web single sign-on, and increases the ability of Oracle9iAS Single Sign-On to support applications running within Oracle9iAS, whether they are designed to use Oracle HTTP Server, Oracle9iAS Portal, or Oracle9iAS Containers for J2EE.
LoginModules provide extensible authentication for Java applications. Developers can create custom authentication modules as required by their application and organization. For example, a Java banking application might require stronger authentication (such as a challenge-response mechanism) than a Web site offering only static content. A developer can create a LoginModule that incorporates a challenge-response mechanism which would integrate the application with other JAAS services.
Once users have been authenticated, it is important to enforce the principle of least privilege--that is, that users should have the fewest privileges necessary to perform their jobs. JAAS includes the following authorization features:
The ability to manage and retrieve authorizations in Oracle Internet Directory allows Java applications to leverage the centralized user provisioning capabilities of Oracle Internet Directory. This lowers the cost of application deployment, because Java applications do not have to create their own user repository, but can use existing user and authorization definitions in Oracle Internet Directory. Java applications can retrieve roles for users from Oracle Internet Directory. Optionally, roles can be hierarchical, which means that a role can be assigned to other roles.
The ability to partition security policy by subscriber supports application hosting. For example, each realm (subscriber) can have its own private, partitioned policy, administered by its own administrator. Then each organization subscribing to a hosted application can create its own users and provide its own authorizations to users. In this example, subscribers cannot create users for other subscribers.
User- and code-based policies allow applications to require that a user only assume particular privileges when accessing particular Java applications from particular locations. This enables Java developers to finely tune their security policies. For example, a banking application may give a user access rights to update bank account information. Rather than give every user authorization to update bank account information--which each user does not need--the application need only enforce that users can only update banking information when accessing a particular digitally signed Java banking application from the banking application directory.
For example, the following code specifies that DBPrincipal SCOTT is granted AllPermission only when SCOTT is running application code originating from http://www.oracle.com/HRApp, that is signed by LARRY.
grant Principal oracle.security.DBPrincipal "SCOTT" Codebase "http://www.oracle.com/HRApp" signed "LARRY" { permission java.security.AllPermission; }
Delegation features support impersonation of a specified user (both RunAsClient and RunAsID) within enterprise JavaBeans, JSPs, and servlets.
RunAsClient means an enterprise bean can be configured to run with the permissions associated with the current client. RunAsID means an enterprise bean can be configured to run with the permissions associated with the specified user (for example, run as "DBAdmin"). This allows developers to enforce "least privilege" in their applications, allowing users only those privileges needed to perform a function. In this way, users can only exercise privileges associated with a well-formed business transaction (an enterprise bean).
Oracle9iAS Web Cache is an innovative content delivery solution designed to accelerate dynamic Web-based applications and reduce hardware costs. Deployed before a farm of Oracle HTTP Servers or globally at the network edge, Oracle9iAS Web Cache uses caching, compression, and assembly technologies to speed the delivery of static and dynamic Web pages. Oracle9iAS Web Cache also provides surge protection, load balancing and failover for Web servers. Combined, these features ensure application performance, scalability and availability, and help to lower the cost of conducting business online.
Using Oracle9iAS Web Cache, e-businesses benefit simultaneously from improved response times and lower infrastructure costs. With Oracle9iAS Web Cache, e-businesses can now serve rich content faster, to more customers, using fewer computing resources than ever before.
As part of the security architecture of Oracle9iAS, Oracle9iAS Web Cache can be configured to accept HTTPS requests from clients and forward them to Oracle HTTP Server.
|
See Also:
|
The following chapters in this document contain conceptual and configuration information about the security features of primary Oracle9iAS elements. If you have installed the necessary software and need to configure the security features of the application server, please refer to the remaining chapters in this document.
If you need information about administering the application server, then please refer to the Oracle9iAS Documentation Library for the appropriate administrator's guide or development guide.
|
|
 Copyright © 2002 Oracle Corporation. All Rights Reserved. |
|