Release 2 (9.0.2)
Part Number A95879-01
Home |
Solution Area |
Contents |
Index |
| Oracle9iAS Containers for J2EE Services Guide Release 2 (9.0.2) Part Number A95879-01 |
|
This chapter describes how the JAAS provider is integrated with applications developed for Java2 environments in Oracle9iAS Containers for J2EE (OC4J).
This chapter contains these topics:
The JAAS provider integrates into applications developed for several Java2 environments:
For developing, deploying, and managing standalone Java applications
For developing, deploying, and managing multi-tier, Web-based applications
When the JAAS provider is integrated with applications developed for the Java2 Platform, the following Oracle components are available to developers:
RealmLoginModule
See Also:
Figure 6-1 provides an overview of an application running in a J2SE environment.
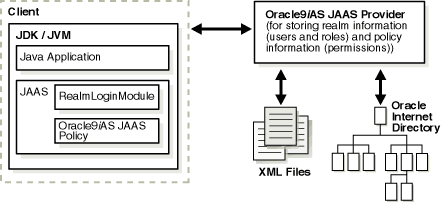
The following section describes the responsibilities of the Oracle components illustrated in Figure 6-1 when a client request is initiated.
RealmLoginModule or other LoginModule authenticates the client's login attempt.
checkPermission() safely.
When the JAAS provider is integrated with applications developed for the J2EE environment, the functionality of the J2SE environment extends to the enterprise level. Additional features in the J2EE environment include:
OC4J is a key component of the JAAS provider integration in the J2EE environment. OC4J is a Web container that accepts HTTP and RMI client connections. These connections permit access to servlets, Java Server Pages (JSPs), and Enterprise JavaBeans (EJBs).
J2EE containers separate business logic from resource and lifecycle management. This enables developers to focus on writing business logic, rather than writing enterprise infrastructure. For example, Java servlets simplify Web development by providing an infrastructure for component, communication, and session management in a Web container integrated with a Web server.
The JAAS provider is also integrated with OC4J to enhance application security. This integration provides the following benefits:
mod_osso or secure socket layer (SSL) and mod_ossl
run-as identity support, delegation support (from servlet to Enterprise JavaBeans)
Another key component of JAAS provider integration in the J2EE environment is JAZNUserManager. JAZNUserManager is an implementation of the OC4J UserManager interface.
JAZNUserManager permits secure replacement for or migration from the OC4J principals.xml file with the following:
For information on using the JAZN Admintool to migrate from
See Also:
principals.xml, "Migrating Principals from the principals.xml File"
In addition to the features mentioned in "Replacing principals.xml", JAZNUserManager provides many other features, including:
RealmLoginModule integration in non-SSO environments
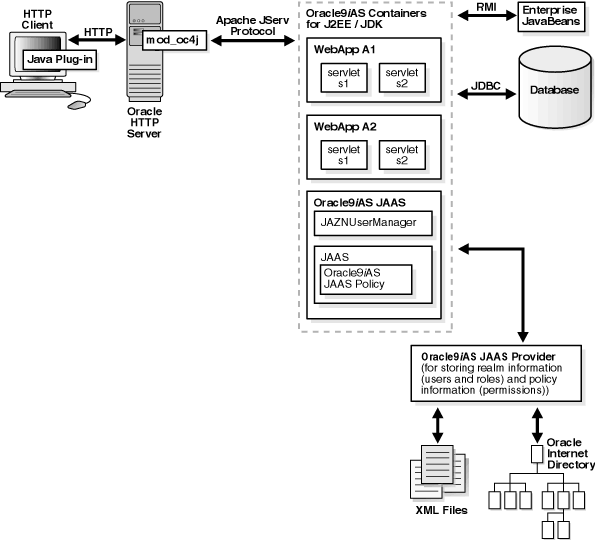
Figure 6-2 provides an overview of an application running in a J2EE environment.
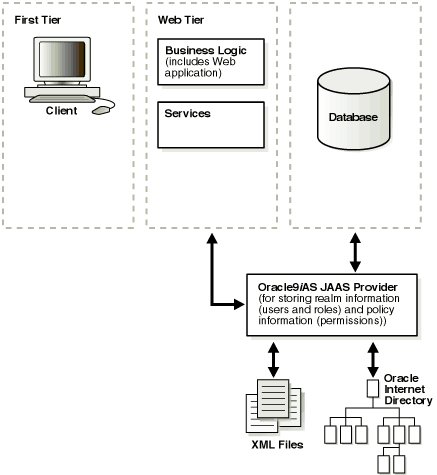
The JAAS provider integrates with three different login authentication environments in a J2EE applications.
The following sections discuss how the JAAS provider integrates with each of these authentication types.
SSO lets a user access multiple accounts and applications with a single set of login credentials. Figure 6-3 shows JAAS provider integration in an application running in an SSO-enabled J2EE environment.
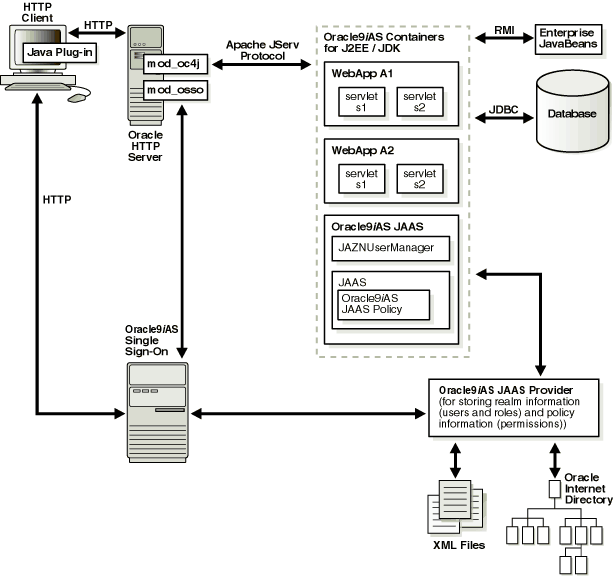
This section describes the responsibilities of Oracle components when an HTTP client request is initiated in an SSO-enabled J2EE environment.
runas-mode in the jazn-web-app element.
If the runas-mode is set to false, then the following happens:
If the runas-mode is set to true, then the following happens:
service() method within a PrivilegedAction block through Subject.doAs(). The JAZNUserManager enforces security constraints.
Subject.doAs() is called, JAAS consults the provider for permissions associated with the SSO user through the getPermissions() method.
AccessControlContext based on the permissions returned from getPermissions().
AccessControlContext of the SSO user.
SecurityManager.checkPermission().
SecurityManager.checkPermission() returns safely and the client HTTP request proceeds.
SSL is an industry standard protocol for managing the security of message transmission on the Internet. Figure 6-4 shows the JAAS provider integration in an application running in an SSL-enabled J2EE environment.
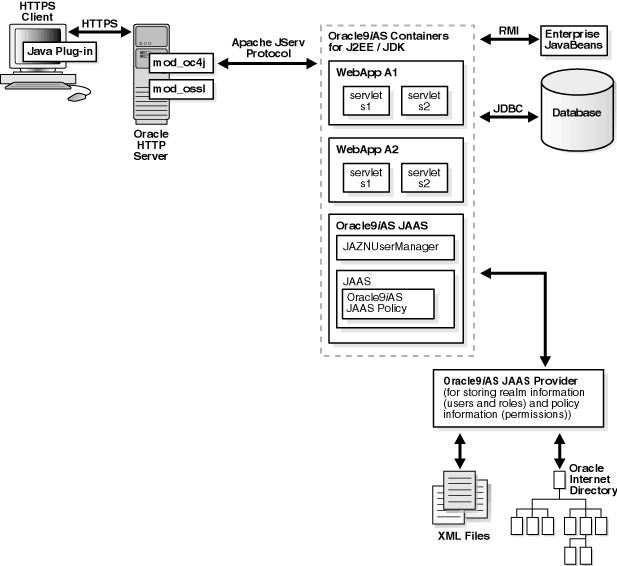
This section describes the responsibilities of Oracle components when an HTTP client request is initiated in an SSL-enabled J2EE environment. In this environment, Oracle9iAS Single Sign-On is not used. A login module (for example, RealmLoginModule) is used.
runas-mode in the jazn-web-app element.
If the runas-mode is set to false, then the following happens:
If the runas-mode is set to true, then the following happens:
service() method within a PrivilegedAction block through Subject.doAs(). The JAZNUserManager enforces security constraints.
Subject.doAs() is called, JAAS consults for permissions associated with the SSL user through the getPermissions() method.
AccessControlContext based on the permissions returned from getPermissions().
AccessControlContext of the SSL user.
SecurityManager.checkPermission().
SecurityManager.checkPermission() returns safely and the client HTTP request proceeds.
Basic authentication bypasses Oracle9iAS Single Sign-On. Figure 6-5 shows specific JAAS provider integration in an application configured for Basic authentication in a J2EE environment.
This section describes the responsibilities of Oracle components when an HTTP client request is initiated in a J2EE environment configured for Basic authentication. In this environment, Oracle9iAS Single Sign-On is not used. A login module (for example, RealmLoginModule) is used.
runas-mode in the jazn-web-app element.
If the runas-mode is set to false, then the following happens:
If the runas-mode is set to true, then the following happens:
service() method within a PrivilegedAction block through Subject.doAs(). The JAZNUserManager enforces security constraints.
Subject.doAs() is called, JAAS consults the provider for permissions associated with the SSO user through the getPermissions() method.
AccessControlContext based on the permissions returned from getPermissions().
AccessControlContext of the user.
SecurityManager.checkPermission().
SecurityManager.checkPermission() returns safely and the client HTTP request proceeds.
Two distinct roles types are available to application developers creating JAAS provider-integrated applications in J2EE environments: J2EE roles and JAAS provider roles. When these role types are mapped together using OC4J group mappings, users can access an application with a defined set of role permissions for as long as the user is mapped to this role.
This section describes these role types and how which they are mapped together.
The J2EE development environment includes a portable security roles feature defined in the web.xml file for servlets and Java Server Pages (JSPs). Security roles define a set of resource access permissions for an application. Associating a principal (in this case, a JAAS provider user or role) with a security role assigns the defined access permissions to that principal for as long as they are mapped to the role. For example, an application defines a security role called sr_developer:
<security-role> <role-name>sr_developer</role-name> </security-role>
You also define the access permissions for the sr_developer role.
<security-constraint> <web-resource-collection> <web-resource-name>access to the entire application</web-resource-name> <url-pattern>/*</url-pattern> </web-resource-collection> <!-- authorization --> <auth-constraint> <role-name>sr_developer</role-name> </auth-constraint> </security-constraint>
JAAS provider roles and Users are defined depending on the provider type, LDAP-based Oracle Internet Directory or XML-based.
For example, with the XML-based provider type, developer is listed as a role element in the jazn-data.xml file:
<role> <name>developer</name> <members> <member> <type>user<type> <name>john<name> </member> </members> </role>
OC4J enables you to map portable J2EE security roles defined in the J2EE web.xml file to groups in an orion-application.xml file.
The roles and users defined in your provider environment are mapped to the OC4J developer group role in the orion-application.xml file.
For example, the sr_developer security role is mapped to the group named developer.
<security-role-mapping name="sr_developer"> <group name="developer" /> </security-role-mapping>
This association permits the developer group to access the resources allowed for the sr_developer security role.
User john is listed as a member of the developer role. Because the developer group is mapped to the J2EE security role sr_developer in the orion-application.xml file, john has access to the application resources defined by the sr_developer role.
You are now ready to get started with the JAAS Provider. To get started quickly, follow the sections in Table 6-1 in the exact order listed:
|
|
 Copyright © 2002 Oracle Corporation. All Rights Reserved. |
|