Release 9.0.2
Part Number A95192-01
Home |
Solution Area |
Contents |
Index |
| Oracle Internet Directory Administrator's Guide Release 9.0.2 Part Number A95192-01 |
|
This chapter discusses how you can exploit the way Oracle Internet Directory stores access control policies to secure applications in a large enterprise and in hosted environments. This chapter contains these topics:
Because Oracle Internet Directory stores access control policies as LDAP attributes, you can set metapolicies controlling who can modify them. This enables a global administrator to assign privileges to administrators of specific subtrees--for example, to administrators of applications in a hosted environment. Similarly, a global administrator can delegate to departmental administrators access to the metadata of applications in their departments. Department administrators can then control access to their department applications.
Thus, you can implement access control on two levels:
In this case, the directory stores access control policies that external applications then read and enforce. When a user tries to perform an operation by using an application, the application verifies that the user has the correct authorization to perform the operation.
In this case, the directory serves as the trusted point of administration for all application-specific access control polices. To govern who can administer the access control policies of specific applications, you set access control policies at the directory level for these applications. Then, when a user attempts to change an application-specific access control policy, the directory verifies that the user has the correct authorization to make that change.
Figure 16-1 shows the relationship between directory access control and the application-specific access control mechanisms in a hosted environment.
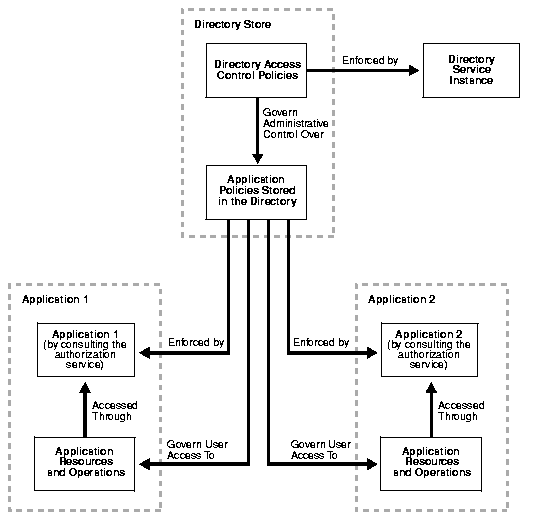
Figure 16-2 illustrates the various domains and the roles associated with them in the directory.
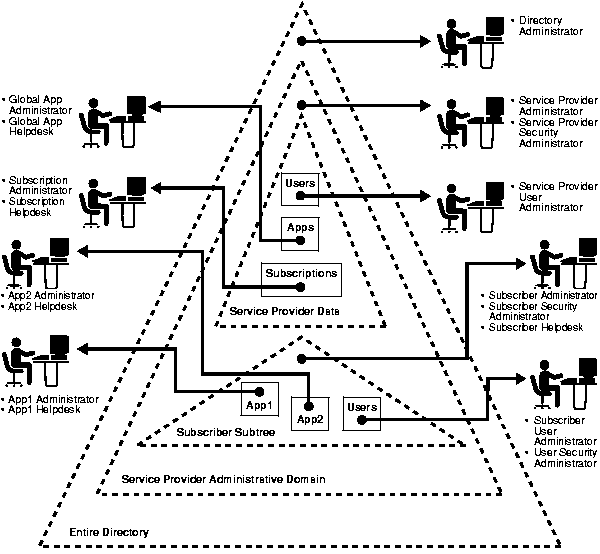
In Figure 16-2, each triangle represents a portion of a DIT.
Figure 16-2 shows only a single subscriber represented in the directory. In reality there are multiple subscribers, each with its own domain requiring protection from the others.
Some of the protection domains in this model are:
These protection domains are supported by the following roles, which enable the service provider or subscriber to customize access control.
These roles have rights to perform activities that span the entire directory.
These roles are limited to the directory trees specific to the subscribers.
When hosting directory-enabled applications, it is not necessary to represent all application-specific roles in the directory. However, it is better that applications, when representing roles that directly affect their directory footprint, follow the delegation model recommendations described earlier. This enables applications to leverage the directory-based delegation model when granting directory-specific privileges to users.
|
|
 Copyright © 1999, 2002 Oracle Corporation. All Rights Reserved. |
|