Release 9.0.2
Part Number A95192-01
Home |
Solution Area |
Contents |
Index |
| Oracle Internet Directory Administrator's Guide Release 9.0.2 Part Number A95192-01 |
|
This chapter discusses password policies--that is, sets of rules that govern how passwords are used.
This chapter contains these topics:
Password polices are sets of rules that govern how passwords are used. The directory server enforces the password policy syntax checks during ldapadd and ldapmodify to ensure that the user password meets the requirements set in that policy. The password policy state checks are enforced by the directory server during ldapbind and ldapcompare. When you establish a password policy, you set the following types of rules, to mention just a few:
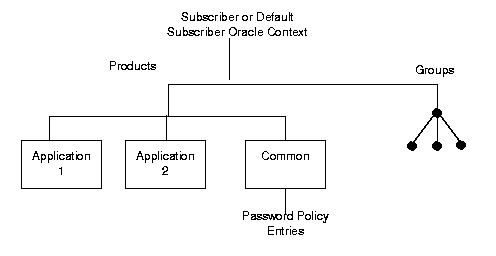
During Oracle Internet Directory installation, the Oracle Universal Installer creates for each subscriber a password policy entry containing all the necessary password policy information. It places this entry as shown in Figure 18-1: immediately below the common entry, which resides under the products entry, which, in turn, resides under the subscriber or default subscriber Oracle context. This password policy is applicable to all users under a given subscriber. The Oracle Internet Directory password policy is applicable only to the userpassword attribute. The orclcommonusersearchbase attribute in the common entry of the subscriber Oracle context must be set to the appropriate value for the password policy to be enforced. This attribute must be set before any password policy modification can take effect.
You establish a password policy by assigning values to the following attributes:
|
Note:
All user passwords are assumed to be single-valued, as mentioned in the July 2001 version of the IETF draft: |
To establish a password policy, you use the pwdPolicy auxiliary object class, which contains password policy information for the entire directory. You set these values during installation. An entry of this object class is created during installation. It has this DN: cn=pwdpolicyentry,cn=my_application,cn=products,cn=Oracle Context,o=my_company,dc=com. In Release 9.0.2, the policy specified applies to the DIT of a given subscriber. Each subscriber can have their own password policy.
This object class contains the following attributes.
Table 18-1 pwdPolicy Object Class AttributespwdMaxAge
pwdGraceLoginLimit
orclpwdAlphaNumeric
pwdLockout
pwdMinLength
orclpwdToggle
pwdLockoutDuration
pwdCheckSyntax
orclpwdIllegalValues
pwdMaxFailure
pwdFailureCountInterval
pwdExpireWarning
The default value for each of these attributes is 0 (zero). These attributes are single-valued, except orclpwdIllegalValues, which is multi-valued.
In addition, the object class top contains these operational attributes, to maintain the user-password state information for each user entry.
pwdChangedtime: The timestamp of the user password creation or modification
pwdExpirationWarned: The time at which the first password expiration warning is been sent to the user
pwdFailuretime: The timestamp of consecutive failed login attempts by the user
pwdAccountLockedTime: The time at which the user account was locked
pwdReset: Requirement for the user to change the password, if this attribute is enabled
pwdGraceUseTime: The time stamps of each grace login by the user
The July 2001 version of the following IETF draft:
See Also:
http://ietf.org/internet-drafts/draft-behera-ldap-password-policy-05.txt
During Oracle Internet Directory installation, a password policy entry is created for each subscriber. Table 18-2 lists and describes the password policy fields in Oracle Directory Manager.
When you create a subscriber, you also configure that subscriber's password policies. Later, you can use Oracle Directory Manager to view, refresh, and modify those policies. However, you cannot add or delete them.
To view a subscriber's password policies, in the navigator pane, expand Oracle Internet Directory Servers > directory_server_instance > Password Policy Management. The navigator pane displays the subscriber password policy entries. The right pane displays a table with two columns:
For the latest updates to a subscriber's password policies, choose Refresh.
For a particular subscriber's password polices, in the navigator pane, choose the subscriber password policy you want to view.
To modify a subscriber's password policies:
This section contains these topics:
The following example enables the pwdLockout attribute, changing it from its default setting of 0 (zero).
The file my_file.ldif contains:
dn: cn=pwdpolicyentry,cn=common,cn=products,cn=OracleContext,o=my_company,dc=comchangetype:modifyreplace: pwdlockoutpwdlockout: 1
The following command loads this file into the directory:
ldapmodify -p 389 -h myhost -f my_file.ldif
Examine the following examples to learn how to view and modify a subscriber's password policies by using command-line tools.
The following example retrieves a specific password policy entry.
ldapsearch -p 389 -h my_host -b "cn=pwdpolicyentry,cn=common,cn=products,cn=OracleContext,o=my_company,dc=com" -s base "objectclass=*"
The following example retrieves all password policy entries:
ldapsearch -p 389 -h my_host -b "" -s sub "objectclass=pwdpolicy"
The following example modifies a password policy entry.
ldapmodify -p 389 -h my_host -v <<EOF dn: cn=pwdpolicyentry,cn=common,cn=products,cn=OracleContext,o=my_company,dc=com changetype: modify replace: pwdMaxAge pwdMaxAge: 100000
|
|
 Copyright © 1999, 2002 Oracle Corporation. All Rights Reserved. |
|