Release 2 (9.0.2)
Part Number A90852-02
Home |
Solution Area |
Contents |
Index |
| Oracle9iAS Portal Configuration Guide Release 2 (9.0.2) Part Number A90852-02 |
|
This chapter provides information about Oracle9iAS Portal after it is installed as part of the Oracle9i Application Server and the tasks that you can perform after installation is complete.
|
See also:
Oracle9i Application Server Administrator's Guide for information about installing Oracle9iAS Portal with Oracle9i Application Server. |
Specific topics covered include:
If Oracle9iAS Portal is installed in the default mode, four Oracle9iAS Portal specific schemas are created. The default base schema name is portal. This name can be changed at installation time.
|
See also:
Oracle9iAS Single Sign-On Administrator's Guide for descriptions of the default Oracle9iAS Single Sign-On Server schemas. |
With each Oracle9iAS Portal installation, a default set of login accounts is created. If the product is installed in a schema named portal, the following default accounts are created:
|
Note: For security reasons, change all the passwords for these accounts after initial login. By default, the password is set to the user name. |
The following groups are created at installation time:
After Oracle9iAS Portal is installed, access it by entering the following URL in your browser:
http://<hostname>:<portnumber>/pls/<dad>
The following table explains the components that make up the URL used to access Oracle9iAS Portal.
|
See also:
|
You can simplify the full URL created by the Oracle9iAS Portal installation to a more memorable or meaningful URL using the Redirect directive. In this way, end users can access Oracle9iAS Portal by entering a simple URL.
By default, the URL for a new Oracle9iAS Portal installation requires you to enter:
http://hostname:portnumber/pls/dad
You can simplify this URL to:
http://hostname/redirectpath
httpd.conf. This file is located in the following directory:
ORACLE_HOME/Apache/Apache/conf/
Redirect /DADnamepath http://hostname:portnumber/pls/dad
For example:
Redirect /portalhome http://mysite.oracle.com/pls/portal
In this example, end users can enter the following:
http://mysite.oracle.com/portalhome
to access the full URL which is as follows:
http://mysite.oracle.com:80/pls/portal
This technique also works with any valid path that is appended to the URL. For example, if you want to display the Oracle9iAS Portal Online Help page group, enter:
http://mysite.us.oracle.com/portalhome/url/folder/ONLINE_HELP
In order for Oracle9iAS Portal to be backward compatible with older portals, the following changes need to be made:
$IAS_HOME/Apache/Apache/conf/mod_oc4j.conf (add it next to the other OC4JMount directives):
OC4JMount /servlet/*
To enable users to create their own portal user accounts, you must configure the self-registration feature.
|
See also:
Oracle9iAS Portal Online Help topic Using Self Registration for information on how to set up Self Registration. |
In earlier versions of Oracle Portal, you could authenticate users against an external repository, With the installation of Oracle9iAS Portal in Oracle9i Application Server Oracle Internet Directory (OID) and the Directory Integration Platform (DIP) is used for all user authentication. OID itself can authenticate against an external repository if that is required.
|
See also:
For an overview of Oracle Internet Directory (OID), refer to the Oracle Internet Directory Administrator's Guide in the Oracle9i Application Server documentation library. |
User and Group information is now stored in OID, while Oracle9iAS Portal objects and privilege information are still stored in Oracle9iAS Portal.
Oracle9iAS Portal needs to subscribe to OID, in order to be aware of any changes in OID data. There are two steps involved in setting up a subscription.
On the OID side, a subscription profile needs to be created. A tool named oidprovtool is provided for this purpose. It will be located in:
ORACLE_HOME/bin
The general syntax for invoking this tool is:
oidprovtool param1=<param1_value> param2=<param2_value> param3=<param3_value>
|
See also:
For a complete example of running the oidprovtool and a list of all the Oracle9iAS Portal specific parameters, refer to Section B.3, "Using oidprovtool to Create a Subscription Profile". |
Once the oidprovtool has been run, a subscription profile is created in OID.
On the database where Oracle9iAS Portal is installed, log on to SQL*Plus with the appropriate user name and password and enter the following command to set up the OID Preferences in the Oracle9iAS Portal schema:
EXEC WWSEC_OID.SET_PREFERENCE_VALUE('DIP_INSTALLED', 'Y')
This updates the OID preferences and after this you can use the Oracle9iAS Portal User Interface in the Global Settings Tab under SSO/OID to update the following two settings:
If you need to customize beyond the above mentioned two settings, you can use oidprovtool. Refer to the Oracle Internet Directory Administrator's guide in the Oracle9i Application Server documentation library, for a complete list of all the possible options for oidprovtool.
The Secure Socket Layer (SSL) enables the securing of HTTP communication between a client and a server. This security is established using a combination of encryption with communication being established through the use of Certificates. Oracle9iAS Portal contains several different parts. Web Cache and the Parallel Page Engine, which act as both clients and servers, while the Oracle9i Application Server acts simply as a server. Each of these different parts must be configured for SSL usage.
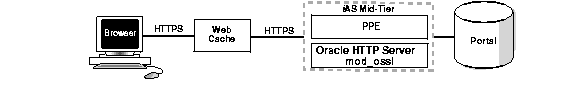
In Figure 2-1 each connection over the network is secured using SSL. There are three communication routes involved in any Oracle9iAS Portall page rendering. Note: For setting up the first two communication routes below, you will need to create an Oracle Wallet.
This is the connection that is seen by the end user when requesting a page from Oracle9iAS Portal. This connection should be secured using an SSL certificate on the Oracle9iAS Web Cache listener.
|
See also:
Oracle9iAS Web Cache Administration and Deployment Guide in the Oracle9i Application Server documentation library for more information on Oracle9iAS Web Cache SSL configuration |
Because a browser can be directed to skip past Oracle9iAS Web Cache server, if the proper port numbers are provided, it is important to configure the Oracle9i Application Server for SSL communication.
|
See also:
Oracle9iAS Web Cache Administration and Deployment Guide in the Oracle9i Application Server documentation library for more information on Server SSL Configuration |
This communication path is already secure based upon the securing of Oracle9iAS Web Cache in the first option above, however there are a couple of configuration items which must be changed for the PPE to recognize the use of SSL.
With HTTPS, you use certificates for ports to increase security.
To set this up, edit the OC4J web.xml file. The web.xml file can be found in the following location:
ORACLE_HOME/j2ee/OC4J/applications/portal/portal/WEB_INF/web.xml
You must set up HTTPS such that it is used by all ports at all times. The Parallel Page Engine must be aware of which port(s) are operating under HTTPS.
To do this, add the following XML block to the web.xml file:
<init-param> <param-name>httpsports</param-name> <param-value>433:444</param-value> </init-param>
Where the port numbers 433 and 444 are replaced by your HTTPS port configuration. Your server only needs to have one port, but two are shown in the above example to show the syntax used for multiple entries. Each port in this list operates using the HTTPS protocol, and must have a certificate created on the Oracle HTTP Server for that port.
|
See also:
|
Oracle9iAS Portal and the Oracle9iAS Single Sign-On Server can be configured to run in HTTPS mode if your portal requires increased security. For optimal performance, you can also choose to have a mixed configuration where Oracle9iAS Portal is run in HTTP mode and the Oracle9iAS Single Sign-On Server is run in HTTPS mode.
Secure Socket Layer (SSL) is responsible for securing Web HTTP communication between a browser and a Web server in plain HTTP over SSL (named HTTPS). Enabling SSL to work with the Oracle HTTP Server is handled by the mod_ssl package which is provided with the Oracle HTTP Server. It uses the URL scheme HTTPS rather than HTTP and a different server port.
|
Note: You must be the portal administrator to enable or disable Secure Socket Layer (SSL) in Oracle9iAS Portal and on the Oracle9iAS Single Sign-On Server. |
|
See also:
Oracle9i Application Server Administrator's Guide for more information on enabling SSL on the server. |
Oracle9iAS Portal maintains the URL prefix of the Oracle9iAS Single Sign-On Server which accesses certain information through HTTP calls from the database, using the UTL_HTTP package. These calls must be done through HTTP rather than HTTPS.
Thus, if Oracle9iAS Portal and the Oracle9iAS Single Sign-On Server are configured to use HTTPS, access to an HTTP port on the Oracle9iAS Single Sign-On Server is still required to support these interfaces. The calls made across this interface are required for the following reasons:
To set this URL prefix, which is called the Oracle9iAS Single Sign-On Server Query Path URL, complete these steps:
If you are using SSL, the default port is 443. With Oracle Portal versions prior to 3.0.8, you need to create two enabler configuration entries, and two corresponding partner configuration entries on the Oracle9iAS Single Sign-On Server. Specify the :443 port for one entry, and exclude it for the additional entry.
To add the additional entry, follow the basic procedure of adding the partner entry on the Oracle9iAS Single Sign-On Server Server using the Oracle9iAS Single Sign-On Server Server Administration user interface, and then add the configuration entry on the Oracle Portal side by running the Oracle9iAS Portal Configuration Assistant in the SSOPARTNERCONFIG mode.
|
Note: This step is only required to support Netscape browsers. Microsoft Internet Explorer does not require this step. |
If you want to setup a virtual host, it can be done in one of two ways:
When the IP name is used, several aliases use the same IP address. In this case, Oracle HTTP Server (or any browser supporting virtual name addresses) looks at the Host field in the HTTP request and determines which of the virtual addresses should be emulated.
However, when SSL is used, the IP name is encrypted. This causes the problem, because the software does not know which decryption key to use since the keys differ by virtual name. If there were 1000 separate virtual addresses supported, then on average the software would try 500 different keys to determine which key to use to decode the message. This is not practical, at least for performance reasons.
https://ssladdress.com/virtualname1/<page desired>).
|
See also:
|
The Oracle Reports Security Portlet is installed as part of the Oracle9iAS Portal installation. Depending on the edition of the Oracle9i Application Server installed, the Reports Security Portlet may be hidden. To show the Reports Security Portlet:
WebDAV is a protocol extension to HTTP 1.1 that supports distributed authoring and versioning. With WebDAV, the Internet becomes a transparent read and write medium, where content can be checked out, edited, and checked in to a URL address. mod_dav is an implementation of the WebDAV specification. The standard mod_dav implementation supports read and write access to files.
The term OraDAV refers to the capabilities available through the mod_oradav module. mod_oradav is the Oracle module that is an extended implementation of mod_dav, and is integrated with the Oracle HTTP Server. mod_oradav can read and write to local files, but also to an Oracle database. The Oracle database must have an OraDAV driver installed. mod_oradav calls this driver to map WebDAV activity to database activity. mod_oradav enables WebDAV clients to connect to an Oracle database, read and write content, and query and lock documents in various schemas.
When Oracle9i Application Server is installed, all required OraDAV parameters are set with values that are designed to enable Oracle database content to be accessed through a web browser or WebDAV client. If necessary, you can later modify the values for required parameters and specify values for optional parameters, if the default values do not meet your needs.
The OraDAV parameters are stored in the oradav.conf file and start with DAV and DAVParam. These parameters are specified within a <Location> directive. The oradav.conf file is included in the httpd.conf file in an include statement.
After Oracle9iAS Portal has been installed as part of the Oracle9i Application Server installation, the oradav.conf file should be populated with a <Location> directive which points to the portal schema. In the following example, the location /dav_portal/portal will be OraDAV-enabled and will (once populated with the correct values) connect to the portal schema so that users can use WebDAV clients to access portal data.
<Location /dav_portal/portal> DAV Oracle DAVParam ORACONNECT dbhost:dbport:dbsid DAVParam ORAUSER portal_schema DAVParam ORAPASSWORD portal_schema_password DAVParam ORAPACKAGENAME portal_schema.wwdav_api_driver </Location>
By default, the Oracle9iAS Portal DAV URL is:
http://hostname:port/dav_portal/dadname/
In the above example, the DAD name is portal (the default). The directive created for the Location is dav_portal/portal and the DAV URL will be:
http://dbhost:dbport/dav_portal/portal/
|
|
 Copyright © 2002 Oracle Corporation. All Rights Reserved. |
|