Release 2 (9.0.2)
Part Number A96115-01
Home |
Solution Area |
Contents |
Index |
| Oracle9iAS Single Sign-On Administrator's Guide Release 2 (9.0.2) Part Number A96115-01 |
|
This chapter describes GUI-based and command-line methods for administering and configuring the Single Sign-On Server and applications enabled by the server. It also describes how to grant administrative privileges.
The chapter covers the following topics:
When Oracle9iAS is installed, five Single Sign-On schemas are created by default. Table 2-1 lists and describes these schemas.
When the Single Sign-On server is accessed for the first time, only one Single Sign-On administrator exists: orcladmin, the iAS superuser. The person installing iAS selects the password for this user at install time. The orcladmin account is used to create other accounts, including accounts for iASAdmins, the group that administers Single Sign-On.
Single Sign-On administrators have full privileges for the Single Sign-On server. Using the Single Sign-On administration pages, they can do the following:
To exercise their privileges, Single Sign-On administrators must be members of the administrative group iASAdmins. This means that an existing member of this group must add a new administrator to it. The Single Sign-On server becomes a member of the group iASAdmins when the server is installed. Use the GUI tool Oracle Directory Manager (ODM) to assign administrative privileges.
To grant administrative privileges to an existing user:
cn=user,cn=users,o=subscriber,dc=com
uniquemembers is an attribute of the entry iASAdmins. As such it defines members of the group iASAdmins.
Figure 2-1 reproduces the interface for granting administrative privileges.
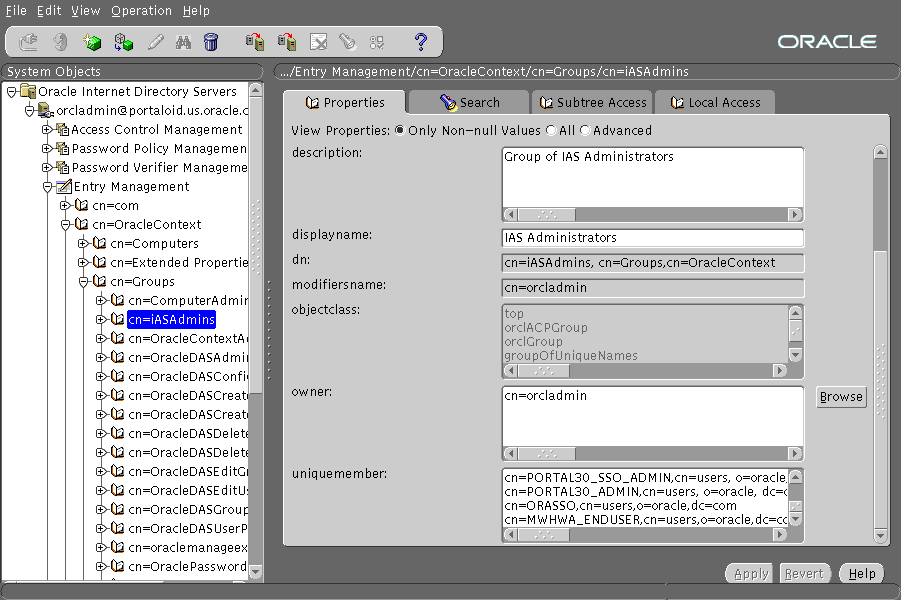
New users are created with a Web tool called Delegated Administration Service (DAS). This tool is accessed at a URL of the following form:
http://host:port/oiddas/
Single Sign-On administrative functions are performed through the Single Sign-On home page.
To access the Single Sign-On home page:
http://host:port/pls/Single_Sign_On_DAD
where host is the name of computer on which the Single Sign-On server is located, port is the port number of the server, and Single_Sign_On_DAD is the database access descriptor for the Single Sign-On schema. The default DAD is orasso.
The Access Partner Applications page appears.
The Single Sign-On Login page appears.
Figure 2-2 reproduces the SSO Server Administration page.
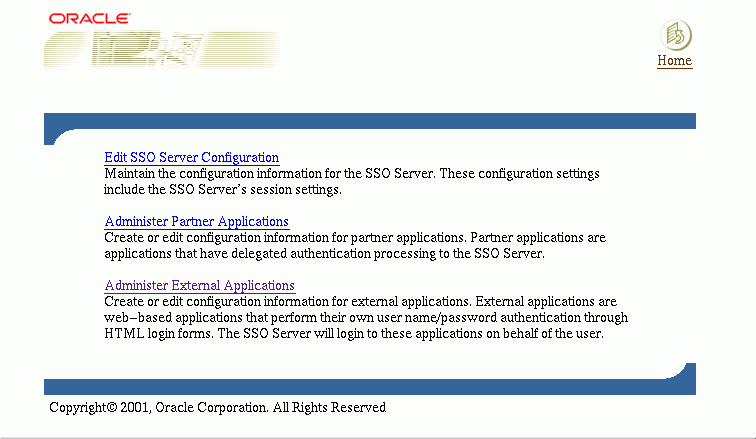
The Edit SSO server page is used to fix the length of Single Sign-On sessions, to verify IP addresses, to enable users to choose territory and language, and to retrieve information about the authentication repository.
To access the Edit SSO Server page, select the link Edit SSO Server Configuration on the SSO Server Administration page.
The Edit SSO Server page contains the following headings and fields:
|
Note: The fields under the heading Authentication Mechanism cannot be modified through the user interface. Instead, see "Changing Single Sign-On Server Settings in the Directory" in Chapter 3, "Directory-Enabled Single Sign-On." |
The Administer Partner Applications page, accessible as a link on the SSO Server Administration page, is used to add, edit, or delete a partner application. Within the Administer Partner Applications page are links for adding and editing applications.
This section covers the following topics:
Selecting the Add Partner Applications link takes you to the Create Partner Applications page. Use the fields on this page, described in the tables immediately following, to register an application with the Single Sign-On server.
Use the following steps to add a partner application:
The Create Partner Application page appears.
The Edit Partner Application page is used to edit configuration information for partner applications.
The Edit Partner Application page contains all of the fields that are in the Create Partner Application page, plus five additional fields in the Partner Application Login section. Table 2-7 describes the additional fields.
Use the following steps to edit a partner application:
"Partner Applications" in Chapter 1, "Single Sign-On Basics"
See Also:
The Administer External Applications page, accessible as a link on the SSO Server Administration page, is used to add, edit, or delete an external application. Within the Administer External Applications page are links for adding and editing external applications.
This section covers the following topics:
Selecting the Add External Application link takes you to the Create External Application page. This page contains the following headings and fields:
Use the following steps to add an external application:
The Create External Application page appears.
If the application uses the Basic authentication method, the User Name/ID Field Name should be empty.
If the application uses the Basic authentication method, the Password Field Name field should be empty.
If the application uses the Basic authentication method, these fields should be empty.
The following example shows the source of the values that are used for Yahoo! Mail.
<form method=post action="http://login.yahoo.com/config/login?6p4f5s403j3h0" autocomplete=off name=a> ... <td><input name=login size=20 maxlength=32></td> .... <td><input name=passwd type=password size=20 maxlength=32></td> ... <input type=checkbox name=".persistent" value="Y" >Remember my ID & password ... </form>
The source provides values for the following:
Login URL: http://login.yahoo.com/config/login?6p4f5s403j3h0
login
passwd
POST
.persistent Y
[off]
Selecting the pencil icon next to an application takes you to the Edit External Application page, where you can edit the values that you entered when you added the application. When you are finished editing, select Apply to enter the changes and to redisplay the page with the updated values.
Each external application expects to receive a user name and password each time the user logs in to the application. To enable single sign-on to these applications, users are given the option of storing their credentials in the Single Sign-On database when they log in to the application.
If Single Sign-On users are logging in to an external application for the first time, they are presented with the External Application Login page. After entering credentials they can select the check box Remember My Login Information for This Application. If they choose this option, the next time they access the application, the Single Sign-On server logs in on their behalf.
Figure 2-3 reproduces the External Application Login page
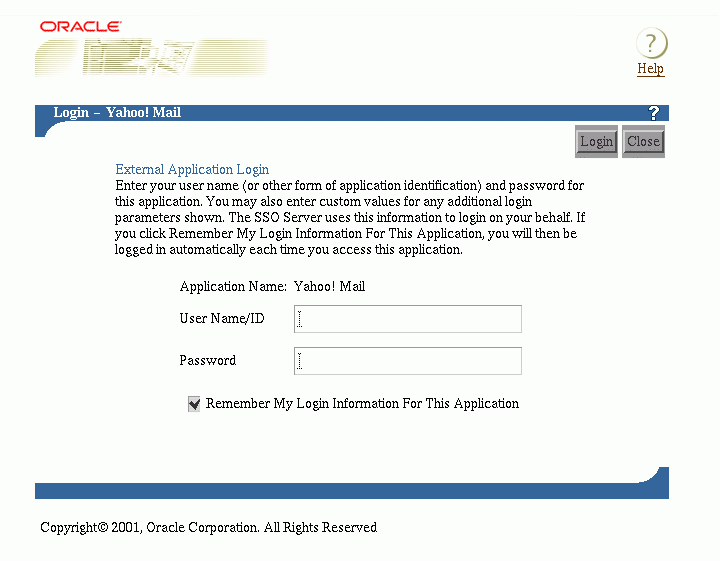
Single Sign-On users and administrators can change their passwords at any time by selecting the Change Password link on the SSO Administration page.
To access the SSO Administration page, user and administrator alike must enter the the URL for the Single Sign-On home page, as explained in "Accessing the Single Sign-On Administration Pages".
The administrator can alter the Change Password page to suit his tastes by following the procedures in Chapter 8, "Customizing the Single Sign-On Interface". For rules governing passwords, see "Password Policies" in Chapter 3, "Directory-Enabled Single Sign-On".
The Single Sign-On administrator can enable users to select from a number languages, including Chinese and other languages encoded in multibyte character sets. These languages can be selected when iAS is installed. If the user chooses a language, territories associated with that language appear at login. This feature enables the user to choose localization settings such as date, currency, and decimal formats.
Users select a particular language at login time. When they select a language, The server sets a persistent cookie in the user's browser. This cookie retains the user's chosen language between sessions. The default language is English.
At the same time, the Single Sign-On server passes the user's language preference as an attribute (accept_language) to partner applications. This attribute enables these applications to set up sessions in the user's chosen language.
If the Single Sign-On administrator has selected the Enable Users to Choose Territory check box on the Edit SSO Server page, links for territories associated with a chosen language appear in the Single Sign-On interface. These links can be used to specify localization settings such as date, currency, and decimal formats.
The global user inactivity timeout is not configured by default. You must enable it by running the script ssogito.sql.
To configure the global user activity timeout:
orasso.
SQL> @ssogito.sql
Once you have completed a transaction, the script furnishes you a summary of the new timeout settings.
on. The path to this file is as follows:
IAS_HOME/Apache/mod_osso/conf/mod_osso.conf
|
See Also:
"Global User Inactivity Timeout" in Chapter 1, "Single Sign-On Basics" |
The Single Sign-On server can be enabled for Secure Sockets Layer (SSL) at install time. If the administrator does not select this option, SSL must be configured manually.
To configure the Single Sign-On server for SSL:
IAS_HOME/sso/bin
Enter the command, using the following syntax:
ssocfg.sh protocol host port [sso_schema_name]
In this case, protocol is https. (To change back to HTTP, use http.) The parameter new_host is the host name of the Oracle HTTP listener for the Single Sign-On server. You can either assign a new host name or use an existing one. The parameter new_port is the port number of the listener, and sso_schema_name is the name of the Single Sign-On schema. The default schema name is orasso. Note from the syntax that this last parameter is optional.
Here is an example:
ssocfg.sh https login.acme.com 443
Port 443 is the default port number for Single Sign-On over SSL.
<IfDefine SSL> <Location /pls/orasso> SSLRequireSSL </Location> </IfDefine>
The dads.conf file can be found at the following location:
IAS_HOME/Apache/modplsql/conf/dads.conf
Some Single Sign-On URLs must be configured so that only browsers on Oracle9iAS Portal and mod_osso hosts can access them. Oracle Portal must be able to show the authenticated user a list of links to external applications. A mod_osso host configured for extended Basic authentication must be able to access these applications. In both cases, the dads.conf file must be modified.
For Oracle Portal, enter the following lines:
<Location /pls/orasso/orasso.wwsso_app_admin.external_apps_list*> Order deny,allow Deny from all Allow from <oracle_portal_host> </Location> <Location /pls/orasso/orasso.wwsso_app_admin.print_fapp_username*> Order deny,allow Deny from all Allow from <oracle_portal_host> </Location>
For mod_osso, enter the following lines:
<Location /pls/orasso/orasso.wwsso_app_admin.get_ext_app*> Order deny,allow Deny from all Allow from <mod_osso_host> </Location>
|
|
 Copyright © 2002 Oracle Corporation. All Rights Reserved. |
|