Release 2 (9.0.2)
Part Number A92171-02
Home |
Solution Area |
Contents |
Index |
| Oracle9i Application Server Administrator's Guide Release 2 (9.0.2) Part Number A92171-02 |
|
This chapter describes how to manage user privileges in Oracle Internet Directory. It contains the following topics:
This chapter describes administering Oracle Internet Directory with respect to Oracle9iAS. If you need details on specific Oracle Internet Directory features and tools, or if you need background information on Oracle Internet Directory, see the Oracle Internet Directory Administrator's Guide.
Oracle Internet Directory is an online directory, which is a specialized database that stores information in a hierarchical format for fast lookup and retrieval. It implements Lightweight Directory Access Protocol (LDAP) version 3, an industry-standard protocol for accessing online directory services.
Oracle9iAS can use an Oracle Internet Directory that is already in use in your enterprise. In such cases, you typically work with the Oracle Internet Directory administrator to set up and manage the Oracle9iAS nodes. The Oracle Internet Directory administrator should read this chapter to be aware of how Oracle9iAS uses Oracle Internet Directory.
In Oracle Internet Directory, "subscriber" has the same meaning as "enterprise":
This chapter uses "subscriber" and "enterprise" interchangeably.
Oracle9iAS uses containers, groups, and privileges in Oracle Internet Directory. You can use them to administer users and groups. You can delegate privileges to other users ("product administrators") so that they can manage their product. For example, you can give privileges to a user to be a Portal administrator. You can have one or more administrators per product.
When you install Oracle9iAS Infrastructure, the installer configures the metadata repository database to use Oracle Internet Directory. Oracle9iAS creates its own area in Oracle Internet Directory. This enables all Oracle9iAS components (for example, Portal, Wireless, and Delegated Administration Service) to access the same data. It also enables an enterprise to centralize security by managing users and applications under one server.
This model is different from Oracle9iAS Release 1.x. In Release 1.x, each component had its own repository of users.
The Oracle Internet Directory that Oracle9iAS uses can be a newly created instance, or you can direct the installer to use an existing Oracle Internet Directory. For example, if you have an existing Oracle Internet Directory instance that you use as a corporate directory and that contains entries for users, and you plan for those users to access applications from Oracle9iAS, then it might make sense to share that Oracle Internet Directory instance with Oracle9iAS.
To distinguish the two types of configuration, this chapter uses the following terms:
In a newly created Oracle Internet Directory, you (the Oracle9iAS administrator) perform Oracle Internet Directory administrative duties.
In an existing Oracle Internet Directory, you and the Oracle Internet Directory administrator work together to manage the Oracle Internet Directory instance.
|
Note: If you are using an existing Oracle Internet Directory instance, you need to upgrade it to Release 9.0.2 before Oracle9iAS can use it. See Oracle Internet Directory Administrator's Guide for instructions on how to perform the upgrade. See also "Upgrading Oracle Internet Directory for Oracle9iAS" for upgrade details specific to using Oracle Internet Directory with Oracle9iAS. |
Oracle Internet Directory contains the following superuser and administrators:
This superuser is allowed to perform all operations in Oracle Internet Directory.
Note that you cannot log in as this superuser using applications that use Oracle9iAS Single Sign-On (such as the Delegated Administration Service application). If you enter "orcladmin" as the user in such applications, Oracle9iAS Single Sign-On authenticates you as the subscriber administrator, whose DN is "cn=orcladmin, cn=user, <Enterprise DN>". To log in as the orcladmin superuser, you use Oracle Directory Manager.
For information on Oracle Directory Manager, see the Oracle Internet Directory Administrator's Guide.
This administrator is allowed to perform all operations in the enterprise subtree. For example, this user can create new users using Delegated Administration Service and assign them privileges.
You can have more than one subscriber administrator. This is typical in cases where you are hosting other enterprises.
For information on Delegated Administration Service, see the Oracle Internet Directory Administrator's Guide.
During Oracle9iAS installation, you specify the password for Oracle Internet Directory superuser and subscriber administrators. The same password is used for these users.
When you manage Oracle9iAS using the Oracle Enterprise Manager Web site, you log in as the ias_admin user. This user is not stored in Oracle Internet Directory. Instead, information about this user (such as its password) is stored separately for each host. The ias_admin password is the same for all application server installations on one host.
To manage users, groups, and privileges in Oracle Internet Directory, you do not need to know the ias_admin user password because you do not use Oracle Enterprise Manager to perform these management tasks. However, the ias_admin password may be used internally to set component passwords within Oracle Internet Directory. For this reason, it is important to adhere to the Oracle Internet Directory password policy when setting the ias_admin password.
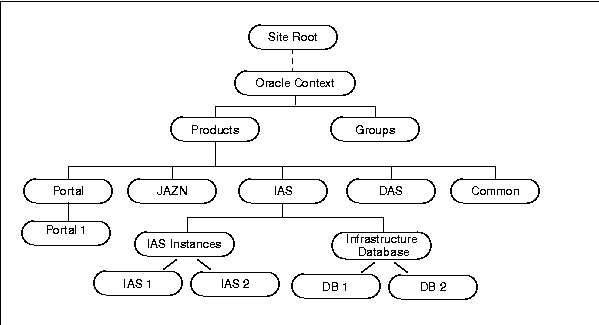
When you install Oracle9iAS Infrastructure, the installer creates the following tree in Oracle Internet Directory (Figure 12-1):
Text description of the illustration securita.gif
Oracle9iAS stores its information in Oracle Context, which is also used by other Oracle products. Immediately below Oracle Context are Products and Groups.
Under Products, there is an area for each component. Each component area has its own component-specific metadata. You do not have to edit anything under Products.
Under Groups, there is node for each access control group. Oracle9iAS uses groups to assign privileges. To enable a user to have a certain privilege, you add the user to the appropriate group. For example, to enable a user to create new users, you add the user to the oracleDASCreateUser group.
You can assign users to have certain privileges at each level of the tree. For example, you can have Oracle Context administrators, IAS administrators, and Portal administrators.
The main administration tasks that you have to perform depend on which mode you are running in. In an existing Oracle Internet Directory, the Oracle Internet Directory administrator performs some of the tasks. In a newly created Oracle Internet Directory, the Oracle Internet Directory installation creates a default configuration to help you perform the tasks.
The following table shows who should perform each task:
| Task | Newly created Oracle Internet Directory | Existing Oracle Internet Directory |
|---|---|---|
|
n/a |
Oracle Internet Directory administrator |
|
|
You do this |
Oracle Internet Directory administrator |
|
|
You do this |
Oracle Internet Directory administrator |
|
|
Done for you |
Oracle Internet Directory administrator |
|
|
Done for you |
Oracle Internet Directory administrator |
|
|
You do this |
You do this |
|
|
You do this |
Oracle Internet Directory administrator |
|
|
You do this |
Oracle Internet Directory administrator |
|
|
Change the application server instance password See "Changing Instance Passwords in Oracle Internet Directory". |
You do this |
Oracle Internet Directory administrator |
You can perform the tasks described in this chapter using Oracle Directory Manager or Delegated Administration Service. These are tools that you can use to manage Oracle Internet Directory. Oracle Directory Manager is a Java-based tool, and Delegated Administration Service is a browser-based tool.
For a complete description of all the tools that you can use with Oracle Internet Directory, see the Oracle Internet Directory Administrator's Guide.
Oracle Directory Manager is a Java-based tool for administering Oracle Internet Directory. You start Oracle Directory Manager with the following command:
(UNIX) ORACLE_HOME/bin/oidadmin (Windows) From the Start menu, select Programs -> ORACLE_HOME -> Integrated Management Tools -> Oracle Directory Manager
The first time you start Oracle Directory Manager, an alert prompts you to connect to a directory server. To connect to a directory server:
If you are logging in for the first time, you need to log in as the superuser (cn=orcladmin).
"Using Oracle Directory Manager" in Chapter 4 of Oracle Internet Directory Administrator's Guide for more information on starting and navigating Oracle Directory Manager.
See Also:
Delegated Administration Service is a Web-based tool that enables you to create and manage users and groups. Users can use this tool to update information about themselves (such as changing their passwords).
To access Delegated Administration Service, point your browser to:
http://host:port/oiddas
host specifies the machine running Oracle HTTP Server.
port specifies the port that Oracle HTTP Server is listening on.
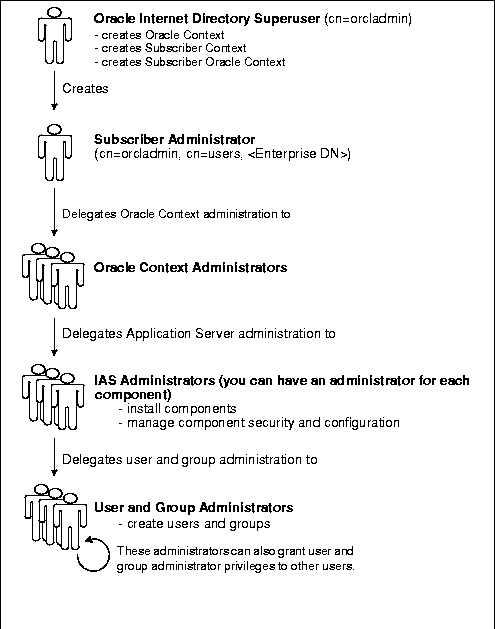
During installation of a new Oracle Internet Directory instance, the Oracle Internet Directory superuser creates the Oracle Context, the Subscriber (or Enterprise) Context, and the subscriber administrator with the appropriate privileges.
You can use the subscriber administrator to delegate administration of the Oracle Context tree to Oracle Context administrators. They, in turn, can delegate administration of Oracle9iAS and its components to Oracle9iAS administrators. The Oracle9iAS administrators have the necessary privileges to install all Oracle9iAS components. The Oracle9iAS administrators can delegate administration of users and groups to other users. Figure 12-2 shows the delegation flow.
If you are working in an existing Oracle Internet Directory, you need to work with the Oracle Internet Directory administrator to ensure that you have the following privileges:
Text description of the illustration securit2.gif
All users who access Oracle9iAS should have a user entry in Oracle Internet Directory. This requirement is mandatory for users who access applications that check authentication and authorization.
Using the subscriber administrator account (which was created during installation) and Delegated Administration Service, you can create users and add them to groups, thus delegating privileges to those users.
You can also delegate user-related operations to other users. To do this, add the users to the appropriate groups, as shown in the following table:
If the Oracle Internet Directory instance also serves as a corporate directory, then it already has users in it. The Oracle Internet Directory administrator is responsible for managing the users.
To create users using Delegated Administration Service:
In a browser, go to:
http://host:port/oiddas
host specifies the machine running Oracle HTTP Server.
port specifies the port that Oracle HTTP Server is listening on.
For details on Delegated Administration Service, see Chapter 9, "The Delegated Administration Service", in the Oracle Internet Directory Administrator's Guide.
You can also create users in Oracle Internet Directory using Oracle Directory Manager. For details, see the section "Adding Entries by Using Oracle Directory Manager" in Chapter 7, "Managing Directory Entries", of the Oracle Internet Directory Administrator's Guide.
If you already have users in Oracle Internet Directory, you can create new users using the procedure described in the section "Adding an Entry by Copying an Existing Entry in Oracle Directory Manager" in Chapter 7 of Oracle Internet Directory Administrator's Guide.
To add a user to a group using Delegated Administration Service:
In a browser, go to:
http://host:port/oiddas
host specifies the machine running Oracle HTTP Server.
port specifies the port that Oracle HTTP Server is listening on.
You can also use Oracle Directory Manager to add users to groups. See Chapter 7 of the Oracle Internet Directory Administrator's Guide for details.
Group memberships define the privileges a user has. To give privileges to a user, add the user to the appropriate groups.
Operations that you can perform on groups are creating groups, deleting groups, and editing properties of groups. To allow users to perform these operations, add the users to the appropriate groups, as shown in the following table:
In an existing Oracle Internet Directory, you may not have group administration privileges because the Oracle Internet Directory administrator has already set up the necessary groups.
In a newly created Oracle Internet Directory, the installer creates groups and associates them with privileges.
In an existing Oracle Internet Directory, the Oracle Internet Directory upgrade process to Release 9.0.2 creates groups mentioned in this chapter, but it does not set up any ACLs in the user namespace because this would override existing ACLs. You and the Oracle Internet Directory administrator can grant the necessary privileges to the groups, or you can associate privileges to existing groups. This section describes the privileges for each group.
Table 12-5 Groups for user administration
Table 12-6 Groups for group administration
To determine which privileges a group has, you can use Oracle Directory Manager. See the Oracle Internet Directory Administrator's Guide for details on Oracle Directory Manager.
Some components in Oracle9iAS need to authenticate users (verify that a user presented the correct password) or to impersonate their clients. The components need the following privileges to perform these operations.
Members of this group include Oracle9iAS Single Sign-On, Unified Messaging, and email server.
Components use proxying so that they are able to read data for that user.
When you install components in Oracle Internet Directory (regardless of whether the Oracle Internet Directory was newly created or existing), the installer adds them to the proper groups. You do not have to add components to groups manually.
When you add or remove components from your Oracle9iAS installation, the installer needs to update the configuration information in Oracle Internet Directory. The user who runs the installer needs privileges in the IAS area in Oracle Internet Directory.
You must be a member of the IASAdmins group, which has privileges to administer the IAS tree in Oracle Internet Directory.
You need to have privileges equivalent to those in the IASAdmins group.
This section describes the upgrade details for Oracle Internet Directory that are specific to Oracle9iAS. For instructions on how to upgrade Oracle Internet Directory to Release 9.0.2, see the Oracle Internet Directory Administrator's Guide.
When you install Oracle9iAS with a new Oracle Internet Directory, the installer installs a new Oracle Internet Directory Release 9.0.2 and configures it for Oracle9iAS. It creates all the groups and sets them up with the appropriate privileges. It also sets up ACLs in the users and the Oracle Context namespaces.
If you upgrade your Oracle Internet Directory to Release 9.0.2 and plan to use it with Oracle9iAS, the upgrade creates ACLs in the Oracle Context namespace, but not in the users namespace. This is to avoid overriding existing policies in the users namespace. It does, however, create groups mentioned in this chapter.
The following ACL policies are not created during the upgrade:
To follow the administration model described in this chapter, you and the Oracle Internet Directory administrator can create the ACLs described in "Group Details" and associate them with the appropriate groups, or you and the Oracle Internet Directory administrator can associate equivalent existing ACLs with the appropriate groups.
The subscriber administrator is also not created during the upgrade process.
For instructions on how to create ACLs in the users namespace and how to associate groups with ACLs, see the Oracle Internet Directory Administrator's Guide.
Oracle Internet Directory enables you to define password policies that are compliant with the security policy of your enterprise.
A password policy is a set of rules for setting and managing passwords. These rules include:
Oracle Internet Directory enforces password policies for its users. You should be aware of the Oracle Internet Directory password policy for two reasons:
ias_admin user. Note that this user is not stored in Oracle Internet Directory; as such, its password is not enforced by Oracle Internet Directory. However, you must follow the same password policy because the ias_admin user password is used internally to create objects in the directory. If the ias_admin user password does not comply with the Oracle Internet Directory password policy, an error occurs.
All users can view the password policy using Oracle Directory Manager:
ORACLE_HOME/bin/oidadmin
If there is more than one "cn=PwdPolicyEntry" entry, select each one and examine the contents of the Path to Password Policy Entry field in the General Tab in the pane on the right side. Select the entry that has "o=DEFAULTSUBSCRIBER" as part of the path in the Path to Password Policy Entry field. Be sure to examine the full path by clicking in the Path to Password Policy Entry field and moving your cursor to the end of the path.
Only the orcladmin user can modify the Oracle Internet Directory password policy.
ORACLE_HOME/bin/oidadmin
If there is more than one "cn=PwdPolicyEntry" entry, select each one and examine the contents of the Path to Password Policy Entry field in the General Tab in the pane on the right side.
Select the entry that has "o=DEFAULTSUBSCRIBER" as part of the path in the Path to Password Policy Entry field.
Individual users can change their own passwords using Delegated Administration Service or Oracle Directory Manager. Oracle Internet Directory superusers and administrators can also change the passwords of other users if they have the appropriate permissions.
Passwords are stored in the userPassword attribute.
See the Oracle Internet Directory Administrator's Guide for details.
You can change the Oracle Internet Directory superuser password using ldapmodify or Oracle Directory Manager.
To modify the password of the orcladmin user in Oracle Internet Directory:
(UNIX) ORACLE_HOME/bin/oidadmin (Windows) From the Start menu, select Programs -> ORACLE_HOME -> Integrated Management Tools -> Oracle Directory Manager
orcladmin user entry in the System Objects frame. The user entry is of the form: username@host:port.
Users can log into Delegated Administration Service to modify their own passwords. The procedure is:
In a browser, go to:
http://host:port/oiddas
host specifies the machine running Oracle HTTP Server.
port specifies the port that Oracle HTTP Server is listening on.
Each application server instance that uses an infrastructure has an entry in Oracle Internet Directory. The instance uses this entry to manage configuration information in Oracle Internet Directory.
Oracle9iAS generates random passwords for the instances in Oracle Internet Directory. You do not need to know what the passwords are because there are no procedures that you need to run that require the passwords.
However, if your corporate security policy requires that passwords be changed on a regular basis, you can use the resetiASpasswd tool to change the password.
To reset the password to a new randomly generated password, execute the following command in the Oracle home of the application server instance whose password you would like to change:
(UNIX) ORACLE_HOME/bin/resetiASpasswd.sh cn=orcladmin password ORACLE_HOME (Windows) ORACLE_HOME\bin\resetiASpasswd cn=orcladmin password ORACLE_HOME
password is the orcladmin password.
ORACLE_HOME is the full path of the Oracle home for the application server instance. Note that this is identical to the Oracle home in which you run the command.
When you deinstall an application server installation using Oracle Universal Installer, the configuration information for the corresponding application server instance is not automatically removed from Oracle Internet Directory. For example, referring to Figure 12-1, "Oracle9iAS Tree in Oracle Internet Directory", if you deinstall the application server installation IAS2 using Oracle Universal Installer, the node named IAS2 is not automatically removed from under IAS Instance in the tree.
It is not a problem to have unused instances in Oracle Internet Directory unless you would like to reuse the same instance name for a subsequent installation. In this case, you must manually remove the instance from Oracle Internet directory before installing the new instance. For example, if you deinstall the IAS2 application server installation using Oracle Universal Installer and would like to install a new installation called IAS2, you must remove the IAS2 instance node from Oracle Internet Directory before doing the new installation.
To remove an application server instance from Oracle Internet Directory:
(UNIX) ORACLE_HOME/bin/oidadmin (Windows) From the Start menu, select Programs -> ORACLE_HOME -> Integrated Management Tools -> Oracle Directory Manager
cn=orcladmin or a user that is a member of the IASAdmins group.
cn=OracleContext.
cn=Products.
cn=IAS.
cn=IAS Instances.
cn=IAS Instances, select the instance you would like to remove.
cn=OracleContext, expand cn=Groups.
cn=IASAdmins.
uniquemember field. Do not select Edit/Delete from the toolbar, rather, edit the uniquemember field with the cursor to remove the instance. Click Apply.
|
|
 Copyright © 2002 Oracle Corporation. All Rights Reserved. |
|