Release 9.0.2
Part Number A95192-01
Home |
Solution Area |
Contents |
Index |
| Oracle Internet Directory Administrator's Guide Release 9.0.2 Part Number A95192-01 |
|
The Oracle Directory Provisioning Integration Service enables applications to receive provisioning information from Oracle Internet Directory.
This chapter contains these topics:
This section describes how the components of an Oracle Provisioning Integration Service environment interact throughout the provisioning process. It contains these topics:
Provisioning is the process of notifying an application whenever user or group data changes in Oracle Internet Directory. Provisioning events arise whenever any change occurs to a relevant user's or group's status or information. An application subscribes to provisioning when it is first installed by creating a provisioning profile in the directory. Subscription occurs once for each application.
Provisioning involves--but is not the same as--synchronization. At times, you may want to synchronize all entities in an application-specific directory with those in the central directory, but provision the application to receive notification only about some of them. For example, the directory for Oracle Human Resources typically contains data for all employees in an enterprise, and you would probably want to synchronize all of that data with the central directory. However, you might want to provision your application to receive notification only when members join or leave a particular group.
In a directory-enabled environment, provisioning involves:
For example, provisioning a user to access an e-mail application involves:
You can change user and group information from any of the following:
User enrollment in an application can happen either automatically or manually.
An example of this is sometimes called "on-demand enrollment." Instead of continuously synchronizing with the central directory, the application creates the user footprint when the user first accesses the application. Oracle9iAS Single Sign-On enrolls a user accessing an application in this way.
The administrator provides application-specific information by using an application-specific administrative tool.
For example, you might want users to obtain their manager's approval before enrollment. In this case, rather than use on-demand enrollment, you might want the application administrator to enroll the user manually after the necessary approvals are complete.
Provisioning a user typically involves creating two kinds of information:
This data includes the user's identity, credentials, profiles, and preferences. It is represented by standard directory user attributes--for example, mailing address or language preferences.
This could include, for example, data in the user's e-mail message folder, or, for the calendaring application, the user's appointment data. It is typically represented by using application-specific conventions either in the directory or in application-specific repositories.
In an Oracle Provisioning Integration Service environment:
To retrieve changes from Oracle Internet Directory, the Oracle Provisioning Integration Service subscribes to the Oracle Internet Directory change log. The changes in the change log are filtered so that only the needed changes get passed to the applications. For example, if an application is interested only in the events of a particular subtree, then the Oracle Provisioning Integration Service notifies it of those changes only.
Figure 36-1 shows the relation between components in an Oracle Provisioning Integration Service environment.
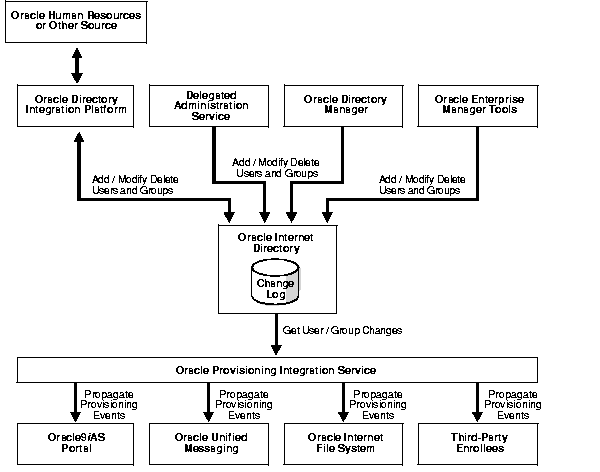
As Figure 36-1 shows:
The Oracle Internet Directory change log records these changes.
The Oracle Provisioning Integration Service monitors Oracle Internet Directory for any changes to user or group information. It conveys these changes to applications in the form of provisioning events.
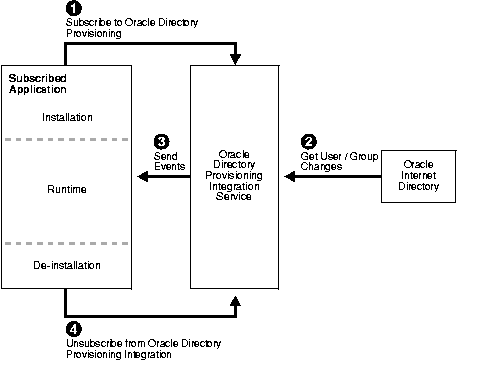
Figure 36-2 shows the life cycle of an application that obtains the provisioning events.
The Provisioning Subscription Tool, oidprovtool, is invoked from any ORACLE_HOME/bin.The general pattern of invoking this tool is:
oidprovtool param1=p1_value param2=p2_value param3=p3_value ...
|
See Also:
"Provisioning Subscription Tool Syntax" for the Provisioning Subscription Tool parameters and the values they can take on |
Once the necessary configuration information is in Oracle Internet Directory, the Oracle Provisioning Integration Service periodically sends the changes to the application. The changes it sends are based on application-specific database connect information.
This section contains these topics:
To deploy the Oracle Directory Provisioning Integration Service, you perform these general steps:
This section describes:
The Oracle Directory Integration Server runs the Oracle Provisioning Integration Service to propagate provisioning events to subscribed applications.
|
See Also:
"Managing the Oracle Directory Integration Server" for instructions about managing the Oracle Directory Integration Server |
Use the Provisioning Subscription Tool to perform these activities:
Use the OID Server Manageability functionality in the Oracle Enterprise Manager to monitor provisioning profiles.
|
See Also:
the following for more details:
|
This section describes the principal entities involved in the provisioning integration process and the directory privileges that they need to complete various operations. It contains these topics:
There are important reasons to control access to the provisioning profiles of applications:
The access that you grant to entities to operate on profiles depends on the delegation needs of the applications. Entities that need controlled access to the provisioning profiles are:
cn=odisgroup,cn=odi,cn=oracle internet directory
cn=Provisioning Admins, cn=Provisioning Profiles...
orclGUID attribute is orclODIPProvisioningAppGUID)
Applications do not automatically have the rights to create provisioning profiles. Rather, only an LDAP identity with privileges to administer provisioning profiles can create them.
Provisioning administrators are modeled as a group and can perform any operation on the provisioning profiles. All other identities have lesser privileges.
Table 36-1 shows the entry-level privileges granted to each entity.
Provisioning profiles contain security-sensitive attributes that need protection from unauthorized access. Table 36-2 describes them.
Table 36-3 describes the access control for the secure attributes for the main entities operating on the provisioning profiles.
The following table shows the access control for all other attributes in the provisioning profiles.
Unlike secure attributes, the other attributes require a less strict access control. Full access is given to all entities involved in the provisioning process: Oracle Directory Integration Servers, provisioning administrators, application entities, and provisioning profiles. All other users receive no access to these attributes.
This section lists and describes the provisioning error messages you may see, and discusses actions to resolve them. These messages appear in the provisioning error messages attribute.
| Message | Reason | Remedial Action |
|---|---|---|
|
LDAP Connection Failure |
The Oracle Directory Integration Platform failed to connect to the directory server. |
Check the connection to the directory server. See Also: "Viewing Active Server Instance Information" to get information about directory server connections |
|
LDAP Authentication Failure |
The provisioning profile is not able to connect to the LDAP Server as administrator |
Verify Oracle Directory Integration Server entry in the directory. Re-register the Oracle Directory Integration Server by using See Also: "Registering the Oracle Directory Integration Server" |
|
Initialization Failure |
Problem in connecting to the directory server using JNDI. |
Look at the trace file for stack trace in |
|
Database Connection Failure |
Problem connecting to the database with the given account information. Either the database is not running or there is an authentication problem. |
Look at the trace file for stack trace in |
|
Exception while calling SQL Operation |
Problem in executing the package. |
Verify the package usability. |
|
|
 Copyright © 1999, 2002 Oracle Corporation. All Rights Reserved. |
|